What is API security?
API security refers to the safeguarding of APIs, both those you own and those you use. But what exactly does that imply?
You've heard of the Internet of Things (IoT), which involves integrating computing power into standard devices. The Internet of Things allows you to connect your phone to your refrigerator, so you know exactly what you need for that last-minute dinner party in an hour when you stop at the grocery store on your way home. Maybe you're part of a DevOps team that uses microservices and containers to build and deploy legacy and cloud-native programs rapidly. Like systems and apps, APIs are one of the most frequent ways for microservices and containers to connect. APIs are becoming more crucial as integration and interconnectedness become more critical.
Why is API security important?
APIs are used by businesses to link services and transfer data. Major data breaches are caused by APIs that are broken, exposed, or hacked. They make sensitive medical, financial, and personal information available to the public. But not all data are built equal, and not all data should be safeguarded in the same way. What kind of data is being exchanged will determine how you approach API security. If your API communicates with a third-party application, learn how that app sends data back to the internet. To use the example above, you might not be concerned if someone discovers what's in your refrigerator, but you could be worried if they use the same API to monitor your location.
Understanding the Potential Risks of APIs
In today's cyber world, API security threats are a typical occurrence. Unfortunately, cyberattacks have become commonplace in today's lexicon. APIs, like any other software, can be hacked, and your data were stolen. APIs are vulnerable to attacks since they serve as gateways for revealing apps for third-party integration. Let's have a look at the top 10 API security dangers to be aware of.
1. Bad Coding
You're exposing yourself to significant API security concerns right away if you start with improper coding. Inefficient code from the start is a sure way to having your API hacked.
2. Inadequate Validation
Validation of SSL certificates is always required to ensure the security of your APIs. Unwanted API traffic interference and insufficient validation will almost probably land you in the hands of a hacker. They can steal your API keys, passwords, and usernames from here.
3. Hesitation Over API Utilization
In large firms, management may overlook the tracking of APIs and their usage statistics. You may pay several expenses and expose yourself to security threats as a result of unprotected APIs.
4. Accountability
Accountability is a difficult concept to grasp. Who is truly responsible for API security risks? The developer is the starting point for the solution. It is the developer's responsibility to design a reliable API. The individual who uses the API, on the other hand, has responsibility. API users can enhance API security by employing additional levels of protection.
5. Risks of XML
It's worth noting that the XML format is linked to the SOAP protocol. This format contains several security flaws that hackers can exploit. To avoid a security breach, it's critical to stay on top of this format.
6. API Incompetence
If API usage isn't recorded, it can become repetitive and redundant. This can result in a necessary financial outlay. API usage requires monitoring, so having solid API governance in place is quite beneficial.
7. Lack of Security
You're leaving yourself open to hackers if you don't use security measures like Transport Layer Security (TLS). It's critical to have encryption protocols in place to safeguard your APIs.
8. Going Overboard with Control
Your API is exposed as soon as API calls are received. Setting restrictions on API password setups, connections and making re-authentication obligatory for overuse is always a good idea. It may appear that you are exercising excessive control, but it is always best to err on the side of caution.
9. Terms to Pay Attention To
Always read carefully and understand the Terms of Service. You won't be fully aware of what your API provides if you don't read up. This may exacerbate issues with the quality of the service they are receiving. In enterprise APIs, data ownership is also mentioned in terms of usage. As a result, skewed data tracking on the customer side may occur.
10. Unsatisfactory Security
Endpoints can remain susceptible, and if security measures aren't in place, any capable hacker will have a field day. To safeguard the security of their API, developers must choose the optimal API format.
Common Attacks Against Web APIs
Following are some common attacks against web apps:
Injection Attacks
Malicious code is implanted in insecure software, resulting in an injection attack. The most well-known examples are SQLi (SQL injection) and XSS (cross-site scripting), although there are others. Injection attacks have long been a problem to online applications, and they are also becoming a significant issue to APIs.
DoS/DDoS Attacks
The attacker attempts to render the targeted system unavailable to its intended users in a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack. They can be scaled in a variety of ways. At one extreme, “slow” DoS attacks can completely deplete a victim's resources while using very little bandwidth. Volumetric DDoS attacks, on the other hand, can involve several terabits per second of incoming traffic. When these attacks are made against well-known websites, they can generate a lot of attention. However, DoS and DDoS attacks against API endpoints are becoming more common.
Data Exposure
Credit card information, passwords, session tokens, private health information, and other sensitive data are constantly processed and transferred by web apps. If an application does not manage data properly, for example, it may be vulnerable by not encrypting it in transit or at rest. This is particularly problematic for RESTful APIs that employ HTTP as their underlying protocol. HTTP includes a variety of actions that could be exploited. An attacker can create malicious requests, change message mapping, and even influence the backend system's answers.
Parameter Tampering
An attacker tries to tamper with the parameters sent between the client and the server. The purpose is to change application data such as user credentials and permissions, product prices and quantities, etc.
Man in the Middle
The attacker intercepts communications between an API endpoint and a client in an API MitM attack. The attacker steals and/or tampers with the confidential information that is exchanged between them.
Unencrypted Communications
Although Transport Layer Security (TLS) is one of the most basic “must-haves” in a secure API, many businesses continue to use APIs that lack it. This offers hackers complete control of the API and the data it processes.
Application Abuse
The attacks mentioned above can be found in a variety of verticals and businesses. There are also dangerous threats that are more particular and tailored to the targeted applications and these. Here's an illustration from the travel sector. Many firms (airlines, aggregators, and so on) provide mobile applications for customers to purchase flight tickets. When a consumer uses an app to reserve a seat, the backend typically reduces the amount of accessible space on the plane right away. The reduction is permanent if the customer completes the reservation and purchases a ticket. Otherwise, it expires after a preset timeout period (usually 10 minutes or so).
Abuse is possible as a result of this. Competitors first reverse-engineer the API. Then they utilize bots to impersonate clients, who start but never finish the flight reservation process. For the duration of the timeout, a seat is removed from the available inventory. During that period, it is unavailable to actual clients. Big blocks of seats can remain unsold when a large number of bots are doing this simultaneously, repeating the operation after each timeout has ended. Bots can block real customers from making purchases.
It's important to note that this type of assault (also known as inventory denial) is based on genuine requests. The bots pose as legitimate users, sending requests to the API endpoint as if they were instances of the app being used by real people on their phones.
Best Practices for Securing APIs
If businesses want to publish their APIs publicly, they must follow specific fundamental security best practices and use well-established security measures.
Make security a top priority
API security should not be a last-minute consideration or viewed as “someone else's problem.” Organizations stand to lose many of their APIs that aren't safe, so make security a priority and incorporate it into the development process.
Keep track of your APIs and manage them
Regardless of how many publicly exposed APIs a company has, it must first be aware of them to secure and manage them. Surprisingly, not all of them are. Conduct perimeter scans to identify and inventory your APIs, then collaborate with DevOps teams to manage them.
Make use of a solid authentication and permission system
Many publicly available APIs suffer from inadequate or non-existent authentication and authorization. When APIs do not enforce authentication (as is commonly the case with private APIs intended solely for internal use), or when an authentication factor (something the client knows, has, or is) is easily broken into, broken authentication happens. Because APIs serve as a gateway to an organization's databases, access to them must be tightly controlled. Use solutions based on robust, proven authentication and authorization mechanisms like OAuth2.0 and OpenID Connect where possible.
Use the concept of least privilege whenever possible
This fundamental security principle states that subjects (people, processes, programs, systems, and devices) should only be given the access they need to perform a specific task. It should be applied to APIs as well.
TLS is used to encrypt traffic
Some organizations may choose not to encrypt API payload data considered non-sensitive (for example, weather service data). Still, TLS encryption should be regarded as essential for organizations whose APIs routinely exchange sensitive data (for example, login credentials, credit card, social security, banking information, and health information).
Remove any information that should not be disclosed
Because APIs are primarily a developer's tool, they frequently contain keys, passwords, and other sensitive data that should be deleted before they're made public. However, this step is commonly ignored. Scanning tools should be incorporated into DevSecOps processes to prevent sensitive information from being accidentally exposed.
Don't reveal any more information than is essential
Whether it's the volume of unnecessary data returned through the API or information that reveals too much about the API endpoint, specific APIs give much too much information. This happened when an API delegated data filtering to the user interface rather than the endpoint. Ascertain that APIs only return as much data as is required to perform their job. Additionally, implement data access limits at the API level, monitor data, and obfuscate if the response contains confidential data.
Implement Web application security
As with any IT system, security monitoring and response is essential whether you are using the APIS offered by other companies or delivering your own services by API. A Web application firewall will stand between your own servers and the rest of the world, so no matter which direction traffic passes, the proxy system will be able to examine the security risk that the access represents.
Graylog API Security – EDITOR’S CHOICE
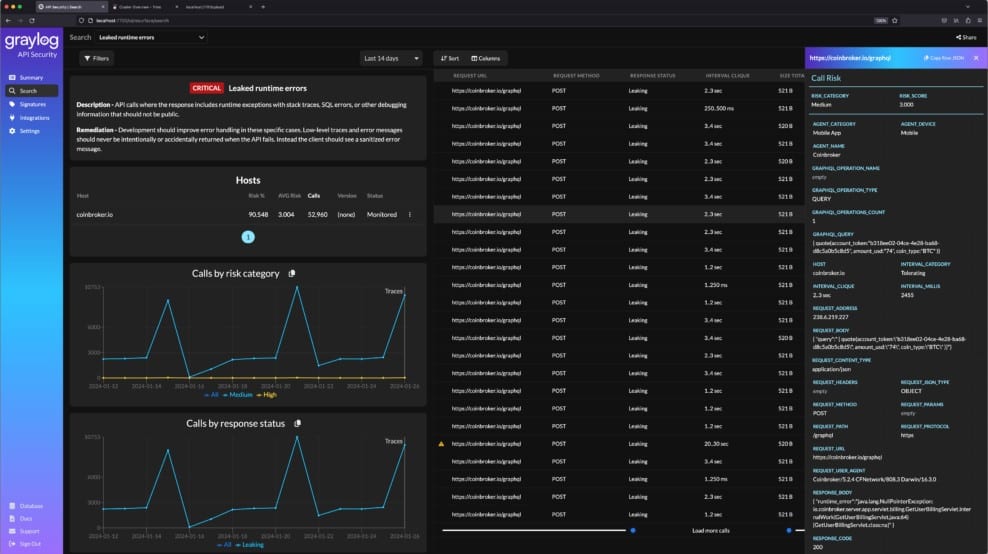
Graylog API Security discovers, assesses, and secures APIs. You probably don’t host or control the APIs that are integrated into the software that you develop. This situation is particularly prevalent in Web applications – you might host your Web application on the cloud and it calls in modules that are hosted elsewhere. In this scenario, you aren’t able to access the code of the API that might have security weaknesses. So, how do you fix them?
This tool locates and documents all of the APIs in your system by reading through your code. It then implements vulnerability scanning, looking for well-known vulnerabilities, such as the OWASP Top 10. It runs the APIS that it can read into, trying different inputs and checking responses. The result of this process is a health check report. Some APIs won’t have security weaknesses, while others will. The tool provides a bug list for APIs with problems.
Key Features:
- Continuous discovery: Scans your software and discovers all APIs
- API documentation: Creates a software component inventory
- Re-scans for new instances: Runs continuously to look for new APIs
- Vulnerability scanning: Checks each API for security weaknesses
- API health report: Some APIs will pass but the tool will produce a bug fix list for APIs with security problems
You probably won’t be able to fix the problems of APIs that are provided by outside businesses. However, you might also find that you can’t run your software without them, or at least, you will need time to replace them. The Graylog API Security package has a solution for this problem.
Security monitoring routines in the package watch the activity of connections to your applications and they will block the connection and ban the source if the activity approaches the security weaknesses that are known about. Both the vulnerability scans and the security monitoring services repeat continuously. So, your APIs are kept secure even if they have security weaknesses.
Pros:
- Vulnerability retesting: Confirms fixes or noted continuing problems
- Inventory updates: Adds new APIs to the inventory when they appear
- Live security tracking: Looks at user activity in relation to known vulnerabilities
- Automated responses: Disconnects sessions in which vulnerabilities might be exposed
- Blacklisting: Bans the sources of suspicious activities
Cons:
- No SaaS option: This is a software package for cloud platforms or for installation over a hypervisor
The Graylog API Security software package will run on cloud platforms, such as AWS, Azure, GCP, and IBM Cloud. You can download the software onto your own server – it runs over MicroK8s hypervisor, which runs on Windows, macOS, or Linux. Graylog offers a Free edition, which is limited, but also serves as a free trial of the paid service.
EDITOR'S CHOICE
Graylog API Security is our top pick for an API Security system because it discovers and documents all APIs in your system and then checks them for security weaknesses. The tool’s discovery and testing services repeat constantly, so the API inventory gets automatically updated and new vulnerabilities get logged. The package then implements live security monitoring that looks at user activity. Knowing where the weaknesses are in your APIs, the package alerts if user actions approach those features and will disconnect the session if it looks as though exploits are going to be implemented. You might not be able to fix API security problems, but you can cloak them.
Download: 1 node and 16GB of local rolling storage FREE Access
Official Site: https://go2.graylog.org/api-security-free
OS: MicroK8s, AWS, Azure, GCP, or IBM Cloud
Indusface AppTrana
Indusface AppTrana is an example of the type of package that you need. It provides malware protection and hacker detection while also absorbing DDoS attacks. This service protects websites and API and there is also a higher plan that provides a managed security service.
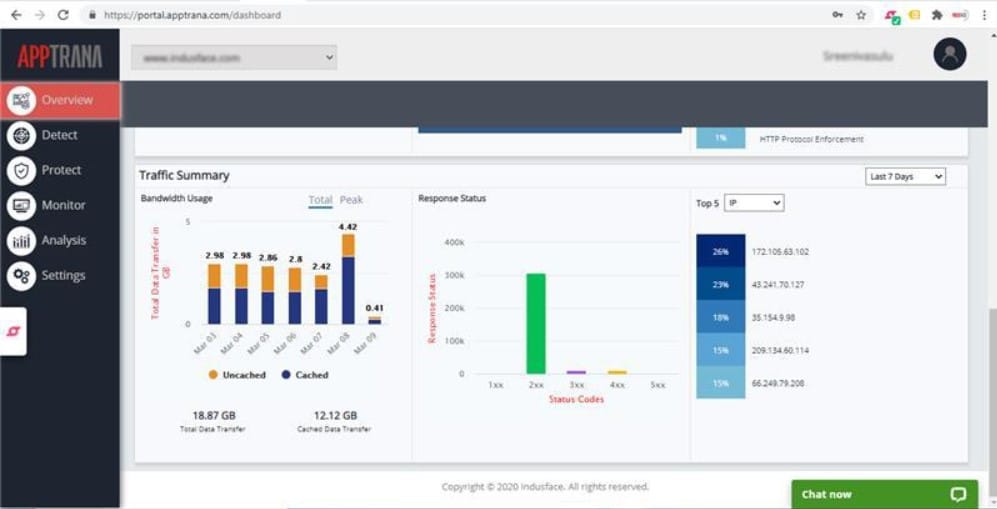
Indusface offer a fully functional 14-day free trial of the AppTrana system.
Conclusion
APIs, particularly for mobile and Internet of Things (IoT) devices, have arguably become the preferred technique for developing modern applications. While the concept of bringing data into a program from a third-party source isn't new, the ongoing evolution of app development methodologies and the need to innovate means that some companies may not yet understand the hazards associated with making their APIs public. The good news is that securing them isn't particularly difficult.
Most businesses currently have countermeasures in place to resist well-known API-targeting attacks such as cross-site scripting, injection, distributed denial-of-service, and others. Many of the best practices listed above will be familiar to experienced security professionals. Start at the top of the list and work your way down if you're unsure where to begin. Your ultimate goal should be to build robust API security standards and manage them proactively over time, regardless of how many APIs your organization chooses to offer publicly.