Cloud security is a top concern for companies today. Did you know that in 2021, about 79% of companies reported at least one cloud data breach? Given that most companies in the world today have a cloud presence, this statistic is sure to ring some alarm bells for you.
So, what can you do to protect your applications, services, virtual machines, and other resources hosted on the cloud? The simple answer – leverage the benefits of cloud workload security platforms.
Here is our list of the best cloud workload security platforms:
- Datadog Cloud Workload Security Analyzes your cloud workload across hosts, containers, and kernel to identify vulnerabilities and accordingly, presents security rules that are the best fit for your environment.
- McAfee Cloud Workload Security This is an advanced platform that provides extensive visibility and protection for your cloud environment, and from on-prem to cloud in a hybrid environment.
- CloudGuard Workload Security CloudGuard is a fully-automated cloud-native security solution that provides unified visibility and threat prevention across all your cloud resources.
- Trend Micro This is a comprehensive platform that secures your workloads in the cloud. It also scales well with your business and helps maintain continuous compliance.
- Prisma Cloud This is a cloud-native security solution that provides complete visibility and data protection throughout your cloud infrastructure.
What is a Cloud Security Workload Platform?
A cloud security workload platform is a set of wide-ranging security practices that protect your cloud-based resources and reduce the chances of attacks. It encompasses best practices such as using encryption, securing the APIs that are used by cloud apps, protecting the consoles, tools, and other infrastructure used by organizations, and more.
The next question on your mind is, how can you implement this cloud security? Many cloud workload security platforms are available and let's look at some of the best ones.
Our methodology for selecting the best cloud workload security platform tools
We've broken down our analysis for you based on these key criteria:
- Emphasis on encryption protocols to ensure data security during transmission and at rest.
- Comprehensive API security features to safeguard interactions between cloud applications.
- Robust protection measures for administrative consoles and tools, mitigating unauthorized access risks.
- Integration capabilities with existing security systems and cloud infrastructure for seamless protection.
- Real-time monitoring and rapid response mechanisms to quickly address potential threats and vulnerabilities.
The Best Cloud Workload Security Platforms
Here are some of the best cloud workload security platforms. We have evaluated them across multiple criteria and believe that the below ones can provide top-notch security for your cloud infrastructure and greatly mitigate attacks.
Which of the above is best suited for your organization? Read the detailed description and feature set of each of these tools before deciding.
1. Datadog Cloud Workload Security
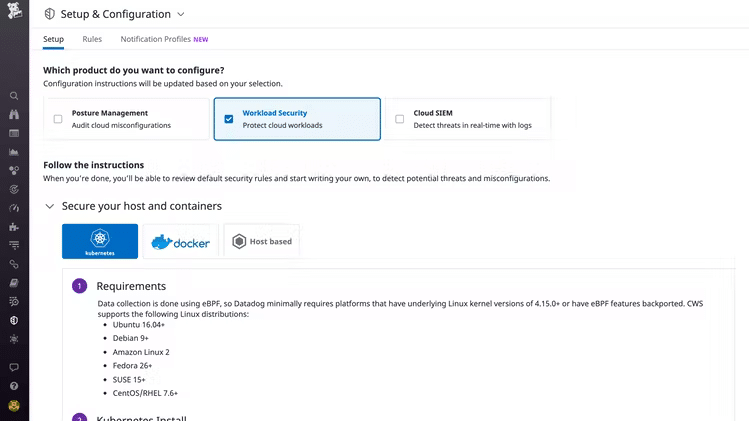
Datadog Cloud Workload Security is a comprehensive platform that performs an in-depth analysis of your kernel and infrastructure to identify any vulnerability. Based on this input, it customizes the existing security rules to present a set of best practices that work well for your cloud environment.
Key Features:
- Monitors Workload Activity Datadog does deep-dive monitoring of your workload activity and in the process, uncovers any threats that may be lurking in your hosts or containers. It also does a thorough in-kernel analysis to identify any hidden vulnerabilities. This platform can also detect errors during runtime. Besides detecting, it also sends alerts along with the complete context, so you can better understand the threat and mitigate it at the earliest.
- Use Out-of-the-Box Rules Datadog has come up with a bunch of security rules and alerts based on common occurrences and vulnerabilities. These rules can form the baseline of your security threat and are automatically included in the Datadog Agent. An advantage of these rules is that you can customize them further to meet your specific requirements.
- Scalable and Flexible A salient feature of Datadog is its scalability. As your cloud presence grows, Datadog can be automatically extended to cover them all without increasing the complexity of monitoring. This improves operational efficiency and reduces costs greatly. Further, you can leverage the 600+ integrations to customize the platform just the way you want.
- File Monitoring File controlling and monitoring are key aspects in the cloud, and it is also a complex task given that your files can be spread across multiple cloud environments. This is where Datadog helps! Its file monitoring capabilities provide deep visibility into all the file-related activities across your cloud environment and detect problems as they come up. It supports both containers and hosts in real-time, and through it, reduces your overhead. It's also highly scalable and grows with your organization.
Why do we recommend it?
Datadog Cloud Workload Security stands out for its in-depth kernel and infrastructure analysis, along with its flexible and scalable security rule customization. This platform is adept at identifying and mitigating hidden vulnerabilities and threats in real-time.
Overall, Datadog is an advanced cloud workload security platform that continuously monitors all aspects of your cloud environment against a set of baseline rules, and alerts you when the values exceed the established threshold. It doesn't just send alerts, but also the context for quick troubleshooting.
Who is it recommended for?
Datadog is particularly suited for organizations that require extensive file monitoring across multiple cloud environments and those seeking a scalable, flexible solution for continuous cloud monitoring and threat detection.
Pros:
- Takes a holistic approach to server performance and health monitoring
- Supports auto-discovery that builds network topology maps and inventory lists in real-time based on devices that enter the network
- Supports both SNMP monitoring as well as packet analysis, giving you more control over monitoring than similar tools
- Uses drag and drop widgets to customize the look and feel of the dashboard
- Robust reporting system with pre-configured compliance templates
Cons:
- Designed for IT professionals, not the best option for non-technical users
Pricing: The base price starts at $15/host/month for the Pro version and $23/host/month for the Enterprise version. There's also a free version that supports up to five hosts and retains metrics for just one day. Based on your needs, you can add on more services and the price will vary accordingly.
Free Trial: Click here to start a free trial.
2. McAfee Cloud Workload Security
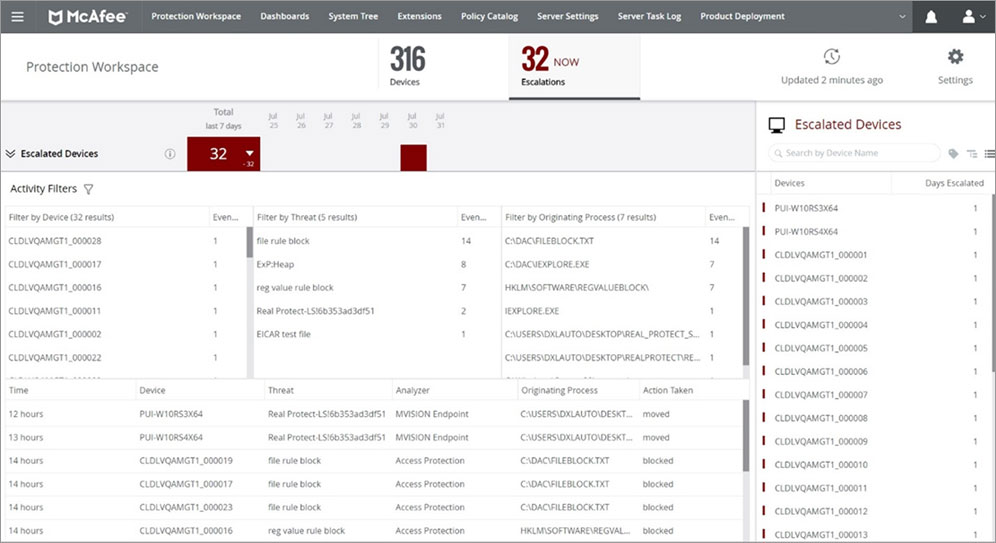
McAfee Cloud Workload Security is a popular platform that provides high levels of visibility and protection for your hybrid cloud environment. It handles end-to-end security and workload from on-prem to the cloud.
Key Features:
- Automates Discovery McAfee comes with automation templates to continuously monitor your workloads and infrastructure. In the process, it identifies vulnerabilities and blind spots and provides protection right from the word go.
- Simplified Management This platform simplifies cloud security management. Besides providing a centralized view of instances across all accounts, it also automates workloads and provides contextual information for easy troubleshooting. Further, its one-click quarantine and single-pane console make it easy to customize security rules as needed across your physical, virtual, and hybrid cloud environments.
- Uses Advanced Security Tools McAfee uses machine learning, VM-optimized malware, file integrity monitoring, and micro-segmentation to protect your workload from possible attacks. Its advanced threat defense can prevent external attacks as well as lateral attacks in the data center. It also uses host-based workload strategies for virtual instances. These strategies, in turn, prevent any issues in the underlying infrastructure.
- Integration McAfee integrates with many cloud providers such as AWS, Azure, and VMware environments. It also supports Chef and shell scripts to deploy your automation. All these make your McAfee platform more extensible and customizable for you.
Why do we recommend it?
McAfee Cloud Workload Security is renowned for its comprehensive visibility and protection capabilities in hybrid cloud environments. It simplifies cloud security management and employs advanced tools like machine learning for enhanced workload protection.
In all, McAfee comes with many advanced features for protecting your cloud, physical, and hybrid environments. Its simplified management and intuitive user interface add to its appeal.
Who is it recommended for?
This platform is an excellent choice for organizations seeking automated discovery and simplified management across data centers and cloud environments. Its integration with major cloud providers and advanced security tools make it suitable for diverse cloud strategies.
Pros:
- Supports Windows, Linux, and Mac OS
- Offers roll-back points for infected endpoints
- Monitors network traffic to stop DDoS attacks, botnets, and rouge mail servers
- Allows sysadmins to orchestrate security policies across their environment
Cons:
- Must contact sales for a quote
Pricing
McAfee Cloud Workload Security offers three plans:
- Cloud Workload Security Basic
- Cloud Workload Security Essentials
- Cloud Workload Security Advanced
Contact the customer team for a quote.
Free Trials/Downloads: There are no free trials or downloads at the time of writing this piece.
3. CloudGuard for Workload Protection
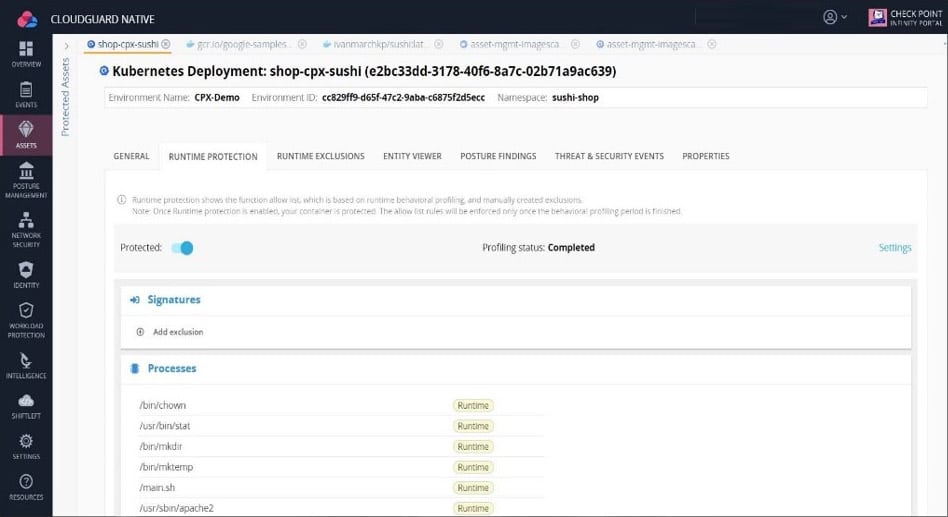
CloudGuard is an automated cloud-native workload solution that provides unified visibility across your entire cloud environment. It comes with threat prevention capabilities and provides compliance with all standards.
Key Features:
- Automated Security This is a cloud-native security solution that provides automated security for containers and cloud applications. It offers comprehensive protection for every cloud layer, so all threats are highly mitigated. Further, it empowers security and DevOps teams to approach this platform with a zero-trust security policy. Such an approach is sure to improve security and compliance.
- Posture Management CloudGuard provides a set of best practices that aligns with NIST and CIS benchmarks. You can even build custom compliance rules that provide visibility into your cloud assets.
- Extensive Workload Protection CloudGuard provides extensive workload protection during runtime. It profiles applications and their functions and continuously monitors their behavior. Further, it checks the functionality and metrics against established baseline values to check for anomalies.
- Elaborate Reporting This platform comes with out-of-the-box report templates that can be used for auditing and compliance. These reports also come in handy for decision-making.
Why do we recommend it?
CloudGuard excels in automated cloud-native workload security, offering extensive workload protection and alignment with NIST and CIS benchmarks. Its detailed reporting and continuous monitoring capabilities are notable strengths.
Overall, CloudGuard Workload Protection continuously monitors your workloads and ensures that their performance metrics are in tune with the established baseline values.
Who is it recommended for?
Ideal for businesses prioritizing automated workload security and compliance, CloudGuard is well-suited for those requiring detailed reporting for audits and a platform that supports both continuous and manual security scans.
Pros:
- Focuses heavily on automated workload security
- Uses NIST and CIS benchmarks to help adjust and monitor your security posture
- Offer highly detailed reporting – great for audits
- Offers both continuous and manual scans
Cons:
- Is more advanced than similar tools – can take time to learn
Pricing: Contact the sales team for a custom quote.
Free Trial: Click here for a free trial.
4. Trend Micro Workload Security
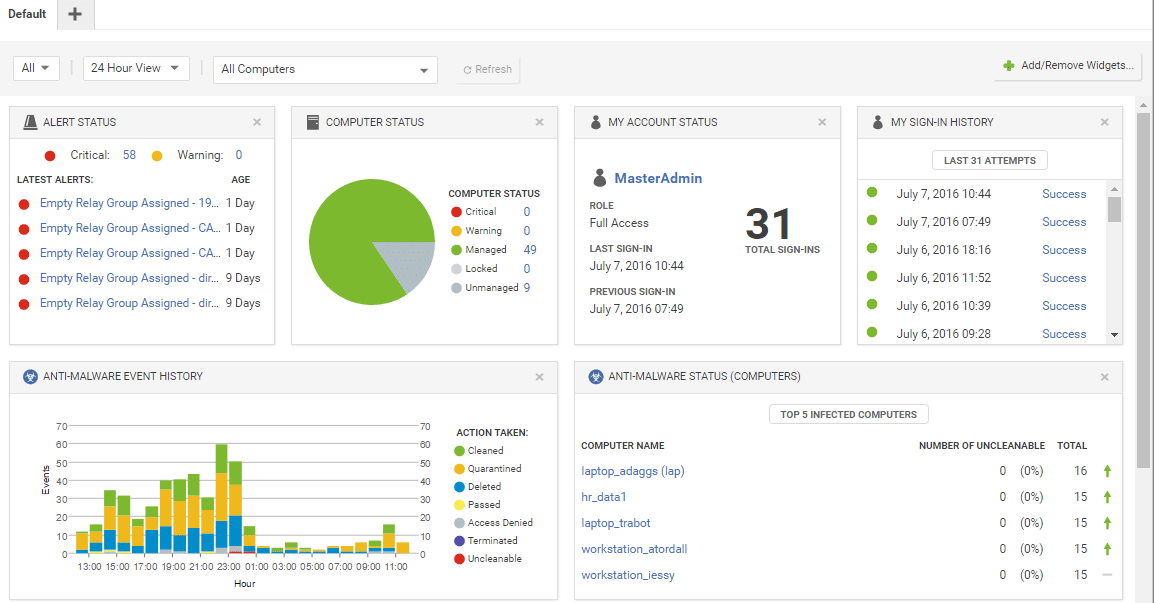
Trend Micro Cloud Workload Security provides comprehensive cloud protection that comes with elastic workloads and containers. Its advanced cloud security capabilities scale well with your business and ensure that you can maintain continuous compliance.
Key Features:
- Automated Processes Trend Micro automates the deployment and discovery of applications. In turn, this automation saves time, improves efficiency, and streamlines compliance. Further, it also simplifies migration and expansion, as needed for your business.
- Highly Flexible Another advantage of Trend Micro is that it is highly flexible and works well with most cloud service providers, integrations, and APIs. this means, you can choose the appropriate cloud, platforms, APIs, and tools for your operations and Trend Micro will monitor them for discrepancies and vulnerabilities.
- Workload Protection This platform constantly monitors your applications, containers, hosts, and other deployments in the cloud. In the process, it identifies malware, ransomware, malicious URLs, and unknown domains that can attack your infrastructure. Another cool aspect is that Trend Micro has an ongoing bug bounty program to identify new errors across a wide range of platforms.
- Comprehensive and Scalable Trend Micro provides a comprehensive and scalable solution. It is as broad as needed to cover your entire infrastructure and also has the depth to manage your cloud security needs. Its scalability also ensures that it grows well with your business.
Why do we recommend it?
Trend Micro provides a comprehensive and scalable cloud protection solution, notable for its automated processes and flexibility across various cloud service providers. It effectively monitors for malware, ransomware, and other threats.
In all, Trend Micro is a good choice if your cloud infrastructure is spread across multiple cloud providers. Also, it is all-encompassing and highly flexible, and scalable to meet your changing business needs.
Who is it recommended for?
This platform is recommended for organizations with infrastructure spread across multiple cloud providers, requiring a unified solution for access control, vulnerability management, and monitoring from a single dashboard.
Pros:
- Unifies access control and vulnerability management across your cloud environments
- Can protect individual runtime environments across multiple containers
- Supports physical, virtual, public, and private cloud environments
- Unifies monitoring of multiple cloud vendors from a single dashboard
Cons:
- Ideal for larger companies utilizing multiple cloud vendors
Pricing: Click here to find a partner near you. This partner can provide a custom quote based on your requirements.
Download: Click here to download a free trial version.
5. Prisma Cloud
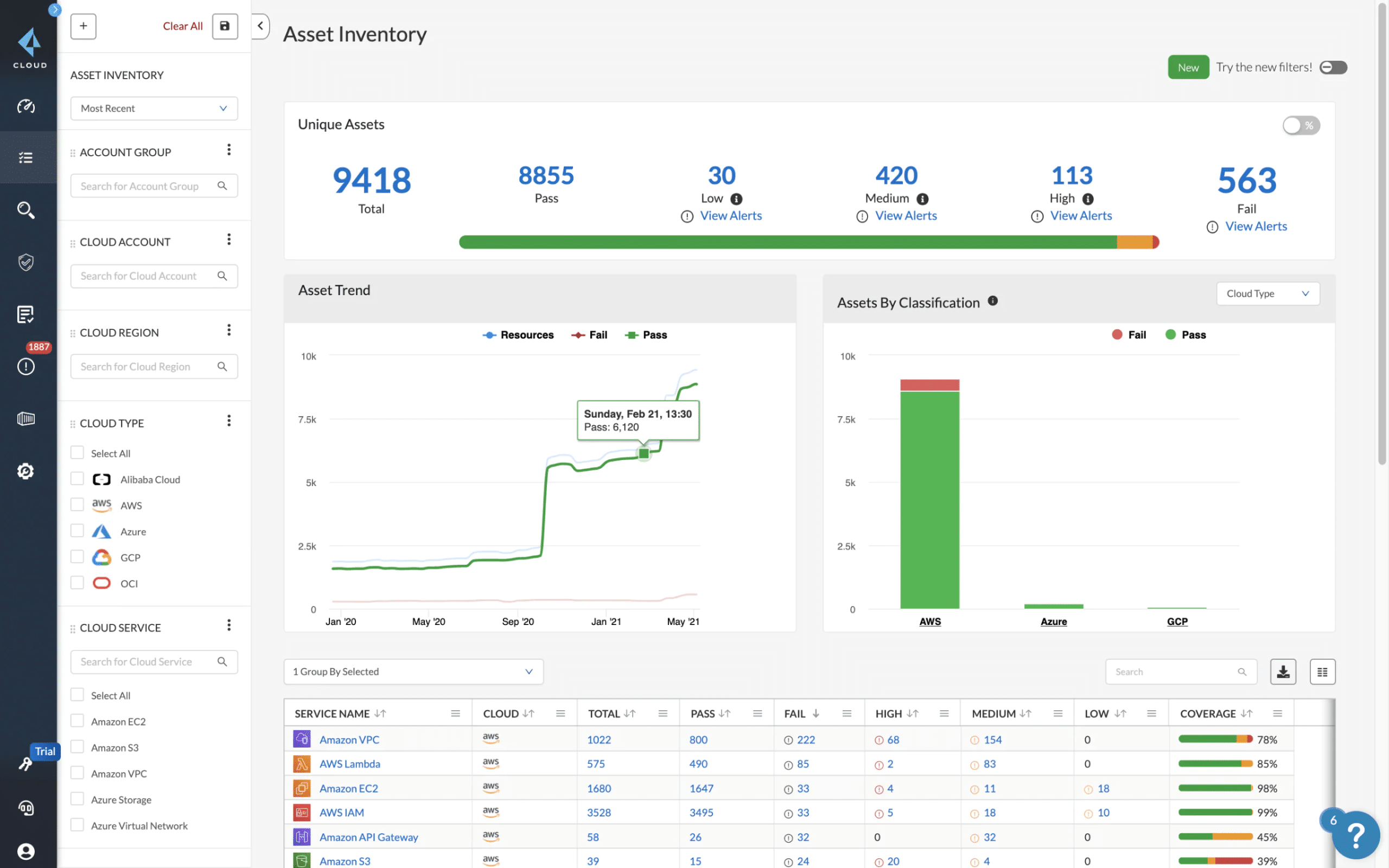
Prisma Cloud is a cloud-native security platform that provides threat protection, compliance, data protection, and visibility to your entire cloud infrastructure. It also comes with many features that simplify the overall management of your cloud infrastructure.
Key Features:
- All-Encompassing Prisma Cloud encompasses not just your applications, but your entire cloud infrastructure even if it's spread across multiple clouds. It is a unified solution that provides unmatched security and visibility through a single pane.
- Complete Lifecycle This platform integrates well with any CI/CD workflow to secure your cloud infrastructure and applications. This flexibility ensures that you can still use Prisma Cloud, even if you change your providers or your infrastructure.
- Simplifies Security Prism Cloud simplifies security by providing all the information you want in a single pane. This greatly simplifies security and compliance as you can find all the information you want in a single pane. Further, the setup process is simple and doesn't entail a lot of time and effort.
Why do we recommend it?
Prisma Cloud offers a cloud-native security platform focusing on automated threat identification and remediation. It integrates well with CI/CD workflows, providing visibility and simplifying security across cloud infrastructures.
In all, Prisma Cloud simplifies your cloud workload security platform without compromising the performance or security of your cloud infrastructure.
Who is it recommended for?
Prisma Cloud is best suited for larger DevOps environments seeking a platform that can detect compliance violations, integrate with Git repositories, and function effectively as a vulnerability detection and management platform.
Pros:
- Focuses more on automated threat identification and remediation
- Can detect compliance violations
- Integrates with your Git repository
- Works well as a vulnerability detection and management platform
Cons:
- Better suited for larger DevOps environments
Pricing: Contact the sales team for a custom quote.
Free Trial: Click here to request a free trial.
Thus, these are some of the well-known cloud workload security platforms. We hope this information gives the insights you need to choose the platform that's best suited for your business needs.
Conclusion
To conclude, cloud workload security platforms are a good option to defend against zero-day and other threats that can impact your cloud infrastructure. Most of these platforms even come with comprehensive reporting for compliance and audits. Needless to say, these platforms continuously monitor your cloud infrastructure and send alerts along with the context for quick troubleshooting.