Running a port scan is essential for knowing exactly what is communicating on your network, and what vulnerabilities you may be susceptible to. In this article, we’ll explore the very best port scanners for both Windows and Linux operating systems. Let’s dive in!
Here’s our list of the best port scanners for Windows and Linux:
- SolarWinds Port Scanner – FREE TOOL A perfect balance between ease of use and detailed port scanning analysis. Download the 100% free tool.
- ManageEngine OpUtils – FREE TRIAL A bundle of tools that are designed to help technicians who are on the move and need more than just port scanning tools. Start a 30-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL Recognized for its comprehensive vulnerability management capabilities, this tool excels in port scanning, assisting IT teams in securing network infrastructures. Its detailed insights into open ports and integrated vulnerability assessment make it indispensable for proactive network security. Start a 30-day free trial.
- Nmap A staple among the security experts and hackers alike
- Unicornscan A tool you may not have heard of that works similarly to Nmap in terms of its syntax and command line-based features.
- Netcat Another great port scanning tool that is arguably just as popular as Nmap and dates back to the early 1990s.
- IP Fingerprints An online port scanning that allows you to scan remote devices with just a few clicks.
- Pentest Tools Another online port scanner tool that allows you to run scans on remote devices.
- Angry IP Scanner Primarily used for network discovery and device identification, it also has port scanning features that can prove useful when used for basic troubleshooting.
What are port scanners useful for?
Port scanners help give a detailed look into a network to determine which ports on a device may be open, what services they are running, and if those ports are compromised or vulnerable to certain exploits.
Hackers and sysadmins alike utilize port scanner tools in a game of a cat and mouse, where attackers will try and take advantage of unsecured ports, and network administrators will attempt to lock down any ports that do not need to be open.
Since ports are common gateways into a network, reviewing your network’s port status and usage is key to ensuring only legitimate services are running on your network. Attackers will often use unsecured ports as entry points, as well as ways to exfiltrate stolen data.
Running a network audit with a trusted port scanner can help identify threats and malware that may have gone undetected by traditional antivirus scans. When using a port scanning tool, make sure you have explicit written permission to run them if you are using them on a network you do not own. In many countries running these tools without permission is considered illegal.
Our methodology for selecting port scanner tool:
We've broken down our analysis for you based on these key criteria:
- Evaluation of ease of use and user interface.
- The breadth and depth of scanning capabilities offered.
- Compatibility with both Windows and Linux platforms.
- Availability of additional features beyond basic port scanning.
- Consideration of both free and commercial options.
The Best Port Scanners
1. SolarWinds Port Scanner – FREE TOOL
The SolarWinds Port Scanner Tool strikes a perfect balance between ease of use and detailed port scanning analysis. Through an easy-to-use interface, you can specify a range of IP addresses or an individual device that you want to scan, and receive a readout of the ports that are open, closed, and filtered, along with the possible services those ports are using.
Key features:
- OS detection
- Multithread scannin
- Intuitive GUI
Why do we recommend it?
SolarWinds Port Scanner is highly recommended for its user-friendly interface and efficient scanning process. It’s particularly suitable for those who need quick and reliable port scanning without the complexity of more advanced tools.
The network sweep completes quickly and uses multithread scanning along with adaptive timing behavior to cut down on the overall scan time. These features also make SolarWinds Port Scanner a great choice for larger enterprise-level networks.
In addition to ports and services, the tool also performs OS detection using its own fingerprinting method. Knowing the operating system of a target device can help attackers identify additional entry points and vulnerabilities in context to the ports that are open on that device.
Scanning results can be saved into multiple formats like XML, XLSX, and CSV, and support IANA port names that can be modified after the scan is finished. For techs or pentesters that find themselves running these scans often, a custom config file can be saved for future use. This template can save IP address ranges and the specific ports you’d like to scan.
The SolarWinds Port Scanner tool offers a simple interface that allows you to get started right away, without having to learn syntax or leave the Windows operating system. Its ease of use and great interface is why this free port scanner tool is number one on our list.
Who is it recommended for?
This tool is ideal for home users, small businesses, and new network technicians who require a straightforward, effective way to conduct port scans without needing extensive technical knowledge.
Pros:
- A completely free tool
- Helps provide a more user-friendly interface to access features similar to Nmap and port scanning
- A better option for new network technicians
- Provides simple outputs based on what port scanning settings you choose
- A good option for home users and small businesses
Cons:
- Not designed for enterprise use, this tool lacks a few features found in their flagship product – SolarWinds Network Configuration Manager.
EDITOR'S CHOICE
The SolarWinds Port Scanner tops our list as it expertly balances ease of use with comprehensive port scanning capabilities. Its intuitive graphical user interface simplifies the scanning process, making it accessible even to those new to network management.
This tool is particularly useful for quickly identifying open, closed, or filtered ports and the services running on them, which is crucial for both security professionals and network administrators. The ability to save scan results in multiple formats, coupled with its OS detection feature, adds to its versatility.
Download: SolarWinds Port Scanner
OS: Windows
2. ManageEngine OpUtils – FREE TRIAL
Rather than a single tool, ManageEngine has put together a bundle of tools that are designed to help technicians who are on the move and need more than just port scanning tools. The OpUtils bundle includes a port scanner, a port mapper (which maps physical connections on a switch), a rogue device detector, an SNMP monitoring tool, an IP address manager, and about six other network-related tools.
Key features:
- Fast scanning
- Bundle of networking-related tools
- Simple and easy to use
Why do we recommend it?
ManageEngine OpUtils is recommended for its comprehensive suite of tools, which includes a fast and efficient port scanner. It's particularly suitable for larger networks and offers additional functionalities like IP address management and physical switch port mapping.
Focusing specifically on just the port scanner, the tool has a clean graphical interface similar to SolarWind Port Scanner, which allows you to quickly pick a range of ports and IP addresses to scan. While the bundle itself may have many different tools, what makes the OpUtils port scanner stand out is its simplicity. With no additional frills, the port scanner will give you a breakdown of the IP address, port status, suspected services, and possible OS in a matter of seconds. The ManageEngine Oputils port scanner also uses fast scan technology, making it ideal for larger networks as well.
Who is it recommended for?
This tool is ideal for network technicians, especially those managing large networks or requiring a range of network management tools beyond port scanning. It's also beneficial for IT professionals who need autodiscovery features for larger deployments.
Pros:
- Designed with large networks in mind
- Offers a suite of tools that provide WoL, IP address management, and physical switch port mapping
- Gathers hostname, device status, and MAC address alongside IP address scans
- Identifies new machines via autodiscovery, great for larger deployments
- Available for both Windows server as well as Linux
Cons:
- ManageEngine is a large monitoring platform that offers a host of tools and features that may take time to fully explore
You can test out the port scanner and all of the tools in OpUtils completely free through a 30-day free trial and is available for both Windows and Linux.
3. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus offers a robust port scanning feature as part of its comprehensive vulnerability management suite. Designed to assist IT security teams in identifying open ports and the services running on them, this tool is an integral part of securing network infrastructure by pinpointing potential vulnerabilities that could be exploited by attackers.
Key features:
- Comprehensive Port Scanning: Quickly scans and identifies open ports across network devices, providing detailed insights into the services and applications that are running on each port.
- Configurable Scan Options: Allows users to customize scanning based on specific needs, including the selection of target ranges, scan intensity, and timing to minimize network disruption.
- Detailed Reporting: Generates detailed reports and visual representations of scanned ports, making it easy to understand the security posture and take necessary actions.
- Integrated Vulnerability Assessment: Beyond just identifying open ports, it integrates with broader vulnerability assessments to provide context and prioritize risks based on the detected services.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is highly recommended for its advanced port scanning capabilities within a larger vulnerability management context. Its ability to perform fast, detailed scans helps organizations quickly identify and address potential security issues. The tool's integration with overall vulnerability management processes ensures that port scanning is not just a standalone task but part of a strategic approach to network security.
Who is it recommended for?
This tool is ideal for IT security teams and network administrators in medium to large organizations who require a detailed and proactive approach to network security. It is particularly valuable for those who need to integrate port scanning into their overall security strategy, ensuring that all aspects of network vulnerabilities are addressed comprehensively.
Pros:
- Efficient and Fast Scanning: Capable of handling large networks with minimal impact on performance
- Detailed Insights: Provides comprehensive details on open ports and the services running on them, which is crucial for effective vulnerability management
- Seamless Integration: Easily integrates with other security measures in the Vulnerability Manager Plus suite for a holistic security overview
- Customizable Scanning: Offers flexibility in scanning configurations to suit various operational environments and requirements
Cons:
- Complexity for New Users: The full range of features and settings might be overwhelming for new users or smaller teams without dedicated IT security resources
- Resource Intensive: High-level functionality may require significant system resources, especially during extensive network scans
ManageEngine Vulnerability Manager Plus stands out for its sophisticated port scanning capabilities, which are part of a broader suite of vulnerability management tools. This integration allows organizations not only to detect open ports but also to understand their security implications fully, making it a critical tool for maintaining robust network security. Start a 30-day free trial.
4. Nmap
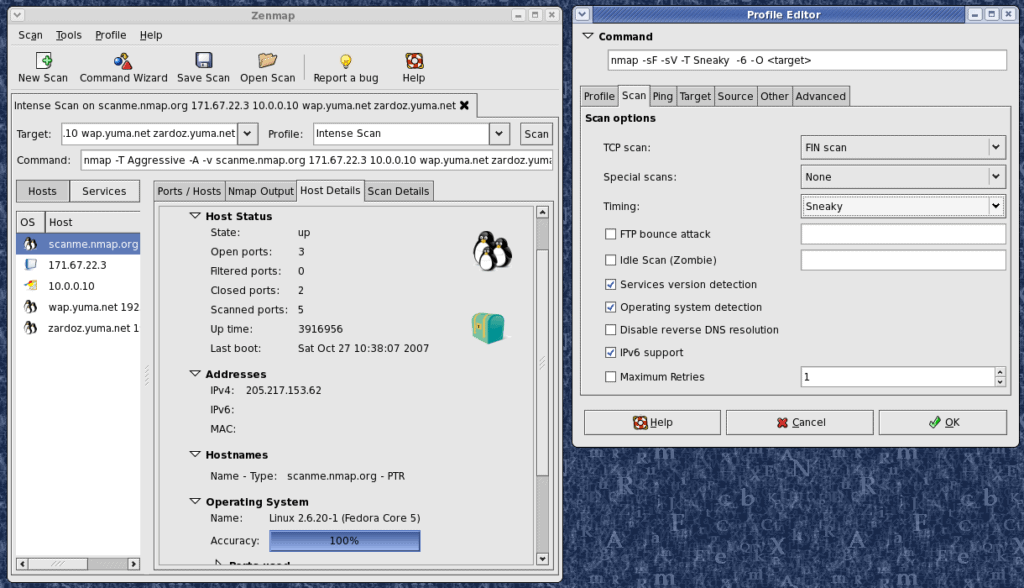
A staple among the security experts and hackers alike is the Nmap port scanner tool. Although it was created in 1997 it still remains popular among red and blue team testers. The port scanner tool is completely free and open-source, allowing anyone to start using it right away.
Key features:
- Lightweight CLI
- Massive open-source community
- Multiple scanning options
Why do we recommend it?
Nmap is renowned for its flexibility and detailed outputs, making it a top choice for both security professionals and network administrators. Its multiple scanning options and large open-source community support make it a versatile and reliable tool.
Unlike our first two tools, Nmap is a command-line (CLI) tool with no GUI that’s designed to leave a very low resource footprint. For those who can't stand the CLI, Zenmap is essentially Nmap but with an interface. Over the years, the open-source tool has gained a cult following community that has kept it up to date by reporting bugs and creating new scanning features over time.
Nmap goes beyond simple port scanning by providing extremely detailed outputs on a port’s status, as well as providing multiple ways to scan a network. There are roughly nine different scan types to choose from, each has its own pros and cons and offers different types of readouts based on what device you're scanning.
For example, instead of just using a UDP or TCP scan, you can stealthily run a NULL scan. This scan sends a packet with headers changed to NULL. Some devices will not know how to handle these packets, giving an opportunity for entry.
These advanced scanning techniques are great to use against your own network, and test to see if your intrusion detection system is actually alerting scans against your network. Nmap is extremely flexible and can be used with Lua programming to script out specific conditions and even automations in some cases.
Who is it recommended for?
Nmap is recommended for security experts and red/blue team testers. Its advanced scanning techniques and scripting capabilities make it suitable for in-depth network security analysis and audits.
Pros:
- Doubles as a security tool, allowing administrators to discover open ports, and applications communicating over ports that are suspicious
- A massive open-source community, Nmap is a very popular networking tool
- Offers a GUI version, Zenmap, which lowers the barrier to entry for new users
- Syntax is straightforward and not difficult to learn for most users
Cons:
- Might be overkill for simpler troubleshooting tasks
- Better suited as a security/auditing tool
The tool is completely free and runs on almost all operating systems including Linux, Windows, macOS, Solaris, and FreeBSD.
5. Unicornscan
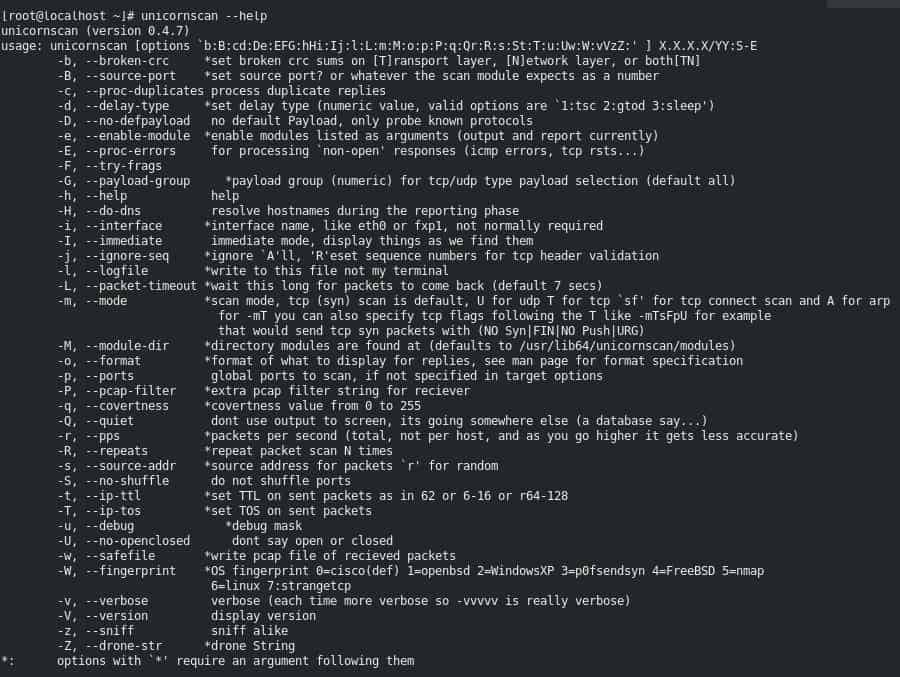
A tool you may not have heard of is called Unicorscan and works similarly to Nmap in terms of its syntax and command line-based features. Outside of a small circle of network security pros, Unicornscan doesn’t get much limelight, but that’s not to say it doesn’t have incredibly useful port scanning capabilities.
Key features:
- Unconventional scanning options
- Lightweight CLI
- Asynchronous scanning
Why do we recommend it?
Unicornscan is recommended for its unconventional scanning options and asynchronous scanning capabilities. It's a great alternative to Nmap, offering similar features with a lightweight CLI.
Just like Nmap, the tool is incredibly lightweight and flexible in terms of scanning networks stealthily asynchronously via TCP and UDP, as well as detecting services and operating systems. Unicornscan is a great option when you’ve hit a proverbial wall with Nmap. The tool offers a number of unconventional scanning and network discovery methods that can recover information missed by other tools when scanning services and remote systems.
Who is it recommended for?
This tool is best suited for network security professionals comfortable with command-line interfaces. It's particularly useful for those seeking different scanning methods or when encountering limitations with other tools.
Pros:
- Easy to use – simple syntax
- Offers features similar to Nmap – a great alternative
- Lightweight CLI
- Well documented – easy to learn
Cons:
- No graphical interface – not ideal for non-technical users
Although there is no interface, those comfortable with the CLI will find the syntax easy to learn and rather intuitive. The tool is Linux only, and can be downloaded via Github, or more simply accessed through the Kali Linux distribution.
Below is an example of the scan results when running Unicornscan:
root@kali:~# unicornscan -mTsf -Iv -r 1000 192.168.0.102:a adding 192.168.0.102/32 mode `TCPscan' ports `a' pps 1000 using interface(s) eth0 scanning 1.00e+00 total hosts with 6.55e+04 total packets, should take a little longer than 1 Minutes, 12 Seconds connected 192.168.103.227:23221 -> 192.168.0.102:445 TCP open 192.168.0.102:445 ttl 128 connected 192.168.103.227:50006 -> 192.168.0.102:443 TCP open 192.168.0.102:443 ttl 128 connected 192.168.103.227:54487 -> 192.168.0.102:161 TCP open 192.168.0.102:161 ttl 128 connected 192.168.103.227:47765 -> 192.168.0.102:80 TCP open 192.168.0.102:80 ttl 128 connected 192.168.103.227:4267 -> 192.168.0.102:1884 TCP open 192.168.0.102:139 ttl 128 sender statistics 963.9 pps with 65536 packets sent total listener statistics 131180 packets received 0 packets dropped and 0 interface drops TCP open http[ 80] from 192.168.0.102 ttl 128 TCP open netbios-ssn[ 139] from 192.168.0.102 ttl 128 TCP open snmp[ 161] from 192.168.0.102 ttl 128 TCP open https[ 443] from 192.168.0.102 ttl 128 TCP open microsoft-ds[ 445] from 192.168.0.102 ttl 128 root@kali:~#
6. Netcat
Netcat is another great port scanning tool that is arguably just as popular as Nmap and dates back to the early 1990s. Despite its age, Netcat is still in use today and supported by a dedicated community that leverages its open-source code to squash bugs and add new features.
Key features:
- Lightweight CLI
- Simple syntax
- Multiple scanning options
Why do we recommend it?
Netcat stands out for its simplicity and flexibility. Its straightforward syntax and ability to perform various scanning tasks make it a reliable tool for both security probing and basic network troubleshooting.
The Netcat port scanner tool gets right to work and skips any fancy features by providing raw command line-based port scanning options. The syntax for Netcat isn’t too difficult to learn and uses simple commands to set different types of scans.
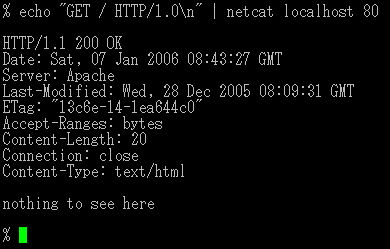
For example: nc -z -v 10.10.5.8 25-150
The above commands would use the -z syntax to only scan for open ports without sending data to them across the ranges of 25 through 150.
The -v reads out the details in verbose:
nc: connect to 10.10.5.8 port 17 (tcp) failed: Connection refused
nc: connect to 10.10.5.8 port 21 (tcp) failed: Connection refused
Connection to 10.10.5.8 22 port [tcp/ssh] succeeded!
nc: connect to 10.10.8.8 port 29 (tcp) failed: Connection refused
nc: connect to 10.10.5.8 port 76 (tcp) failed: Connection refused
Connection to 10.10.5.8 80 port [tcp/http] succeeded!
The results are fairly simple and easy to read, considering the entire tool is used from a CLI. While it isn’t as simple as SolarWinds or ManageEngine, you have a whole lot more flexibility in how the scan is performed, which makes it more geared for security professionals versus a junior technician troubleshooting a network.
Who is it recommended for?
Netcat is recommended for security professionals and network administrators who need a versatile, cross-platform tool for probing network endpoints and conducting security tests.
Pros:
- Available cross-platform for Windows, Linux, and Unix operating systems
- Simple syntax, easy to learn for beginners
- Doubles as a security tool, allowing users to probe endpoints and create backdoors
- Supports file transfer between host and client
Cons:
- NetCat might be overly complicated for users looking for a simple IP scanner
7. IP Fingerprints
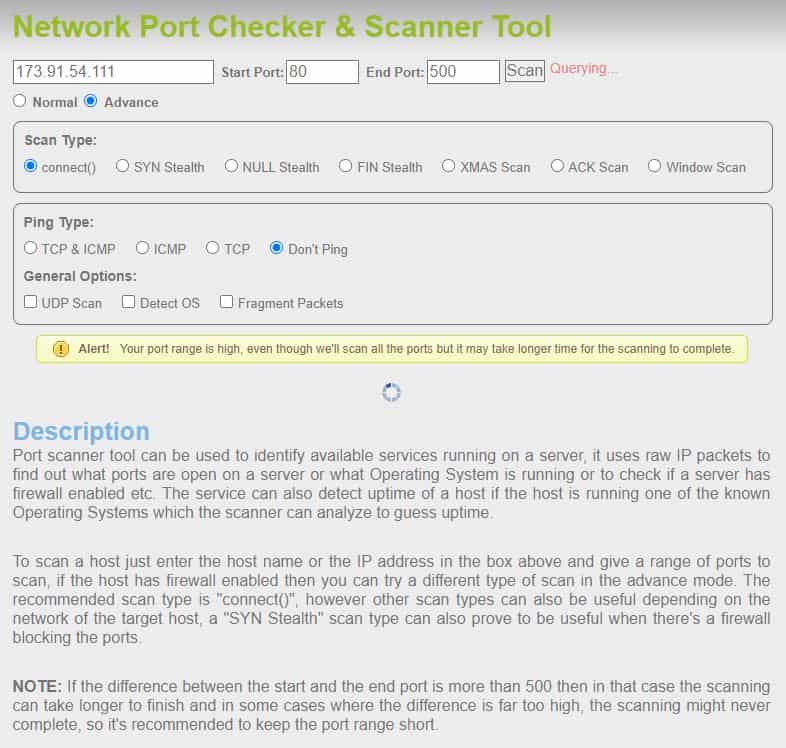
IPFingerprints is an online port scanning that allows you to scan remote devices with just a few clicks. This tool is entirely free and gives you a few simple options to scan either a single port or a range of ports on a targeted device. While most online tools don’t offer additional scanning modes, IPFingerprints offers multiple different scanning options.
Key features:
- Online tool
- Advanced scanning options
- OS and service detection
Why do we recommend it?
IP Fingerprints is an excellent choice for remote, online port scanning with advanced options. Its ability to perform complex scans like SYN, ACK, and FIN, and its OS and service detection capabilities, make it a unique online tool.
You can cycle through SYN, NULL, FIN, XMAS, ACK, and simple ICMP ping scans from the advanced menu option. You can also choose to toggle on or off OS detection, as well as the choice to send fragmented packets to avoid intrusion detection systems. You can think of IPFingerprints as a sort of online Nmap, without needing to actually download Nmap.
A downside to this tool is that it can take a long time to complete the scans, especially for larger port ranges. Considering the tool is completely free it’s a tough online option to beat, especially if for whatever reason you cannot download and install a tool. While most online tools lack any real depth, IPFingerprints is surprisingly useful for port scanning online.
Below is an example of a readout from the results scanning ports 80-5000. This tool took about 10 minutes to produce these results.Host is up (0.095s latency).
Not shown: 911 closed ports PORT STATE SERVICE 80/tcp open http 111/tcp filtered rpcbind 135/tcp filtered msrpc 136/tcp filtered profile 137/tcp filtered netbios-ns 138/tcp filtered netbios-dgm 139/tcp filtered netbios-ssn 445/tcp filtered microsoft-ds 513/tcp filtered login 520/tcp filtered efs
Who is it recommended for?
This tool is ideal for users who need to conduct port scans remotely without the ability to install software. It's suitable for quick scans and those requiring advanced scanning options in an online format.
Pros:
- Available online through your browser, no installation needed
- Can scan a custom range of ports
- Supports complex scans such as SYN, ACK, and FIN
- Can scan using fragment packet to avoid detection
Cons:
- A larger scan exceeding 500 ports can take a long time, in our test this took upwards of 15 minutes
- Lacks graphical reporting options
8. Pentest Tools
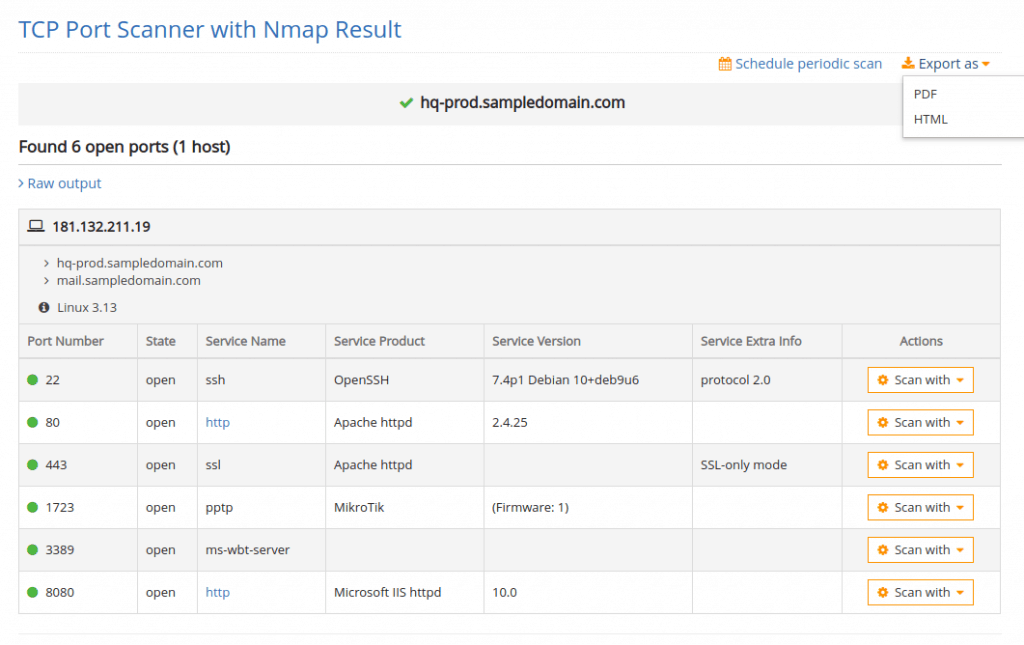
Pentest Tools is another online port scanner tool that allows you to run scans on remote devices. Unlike IPFingerprint, the results you receive for free are less detailed and are only included behind a paid version of the tool.
Key features:
- Done for you scanning
- Full scanning done across all ports
- Online tool
Why do we recommend it?
Pentest Tools is recommended for its comprehensive scanning capabilities and ease of use. It's particularly useful for security professionals who require detailed port scanning across all ports and additional security analysis.
Under the free version, you can view the results of the top 100 ports, but considering most sysadmins use nonstandard ports for specific services, this leaves us in the dark for many other ports and services.
Pentest Tools requires you to pay to view the full results of the port scan results, which includes all 65535 ports of a device as well as a full traceroute. This tool almost feels more like a service, which is fine if you’re non-technical, but not worth it if you’re knowledgeable with any other port scanning tool.
Plans are offered in four different tiers and start at $65.00 per month. Considering there are so many free port scanning tools available, Pentest Tools might be worth it if you want a hands-off approach to port scanning, and simply want results delivered to your inbox.
Below are the results provided by the free version of Pentest Tools:
Starting Nmap ( https://nmap.org ) at 2021-02-23 21:40 EET NSE: Loaded 40 scripts for scanning. Initiating Ping Scan at 21:40 Scanning XX.XXX.XXX.XXX [4 ports] Completed Ping Scan at 21:40, 0.23s elapsed (1 total hosts) Initiating SYN Stealth Scan at 21:40 Scanning ec2-XX-XX-XX-XX.compute-1.amazonaws.com (XX.XXX.XXX.XXX) [100 ports] Discovered open port 443/tcp on XX-XX-XX-XX Discovered open port 80/tcp on XX-XX-XX-XX Increasing send delay for XX-XX-XX-XX from 0 to 5 due to 11 out of 15 dropped probes since last increase. Completed SYN Stealth Scan at 21:40, 22.63s elapsed (100 total ports) Initiating Service scan at 21:40
Who is it recommended for?
This tool is suited for security professionals and those who prefer a hands-off approach to port scanning, looking for detailed results without the need for technical expertise in port scanning tools.
Pros:
- Designed for security professionals
- Completely free and anonymous scanning
- The free scan includes the top 100 ports
Cons:
- Suited more for security professionals
9. Angry IP Scanner
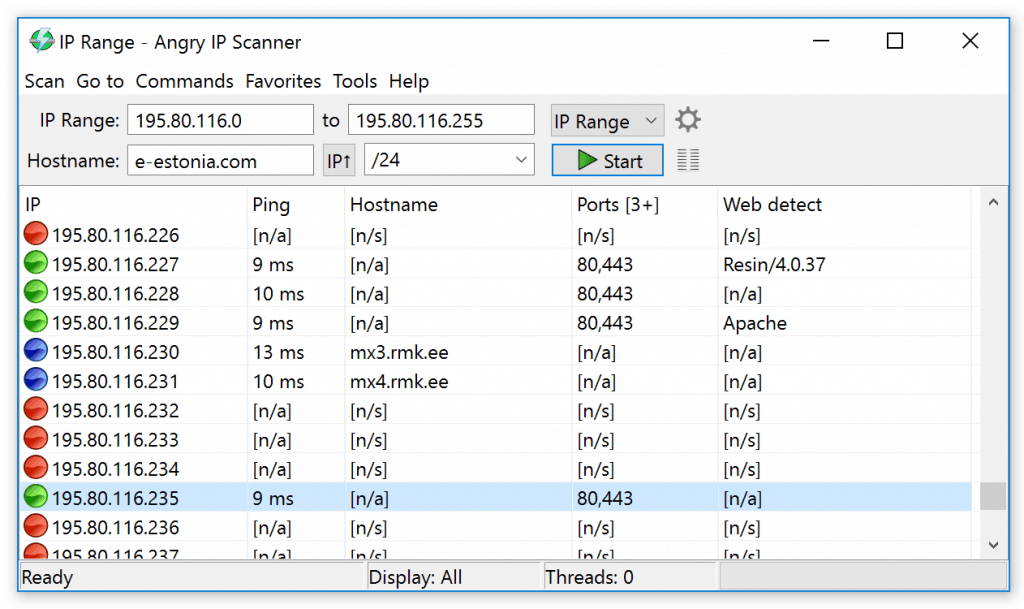
Angry IP Scanner just made it on our list due to its ease of use, and a massive number of users. While Angry IP Scanner is primarily used for network discovery and device identification, it also has port-scanning features that can prove useful when used for basic troubleshooting.
Key features:
- OS detection
- Multithread scanning
- Simple graphical interface
Why do we recommend it?
Angry IP Scanner is recommended for its ease of use and quick scanning capabilities. Its simple graphical interface and multi thread scanning make it a great choice for basic network discovery and troubleshooting.
In a matter of seconds, Angry IP Scanner uses multithreading scan technology to quickly find new devices within the specified range of IP addresses you set. Once finished, you’ll have a neat output of all devices, their online status, hostname, service, and open ports. For a quick at-a-glance look at a device's port details, Angry IP won’t let you down.
Along with the device port status, the tool also uses red and green indicators to signal to you if the device appears to be online and responding to ping commands. Outside of just port scanning the tool is great at tracking down devices that have lost their IP address, or finding those pesky printers that were never set statically.
Who is it recommended for?
This tool is best suited for individuals or small businesses needing quick, one-off scans of smaller networks. It's also beneficial for those looking for a tool to identify devices on a network with minimal configuration.
Pros:
- Easy to install and use – great for a mobile toolkit
- Better suited for one-off scans of small networks
Cons:
- Lacks advanced features such as DHCP reconciliation and rouge DHCP identification
- Doesn’t scale well in large environments
- Lacks detailed reporting that’s useful in enterprise networks
The Angry IP Scanner tool is open source, and available for Windows, Linux, and macOS.
Conclusion
Even with the eight best port scanners, how do you know which one is right for you?
For nearly all use cases, SolarWinds Port Scanner is a great free tool tailored for sysadmins who are looking to audit and discover what ports and services are open on their network. Its design is intuitive, and backend scanning features are built to scale across large enterprise networks.
For those looking to run a simulated attack or penetration test on their own network, Nmap offers some of the best scanning options combined with detailed documentation and community support for those who are just learning about network security.
Lastly, for those who are familiar with Nmap and looking for something new, check out what Unicornscan can bring to the table.
Do you prefer a command line or GUI port scanner tools? Let us know in the comments below!