SIEM tools are crucial components in any data security strategy. They centralize all security events, logs, and alerts into a single place, aggregate data, analyze it, and attempt to identify abnormal behaviors or potential threats. A SIEM tool provides the bird's view to help identify those unusual and often hard-to-see threats.
In this post, we will be reviewing the best SIEM tools. Those leaders and innovators in the SIEM market keep improving and redefining the rules of SIEM.
Here’s our list of the Best SIEM Tools:
- SolarWinds Security Event Manager – FREE TRIAL A SIEM virtual appliance for monitoring and managing network security. It provides log management, advanced analytics, and more. Get a fully functional 30-day free trial.
- ManageEngine Log360 – FREE TRIAL This on-premises system includes Active Directory management as well as a full SIEM. Runs on Windows Server. Start a 30-day free trial.
- Heimdal Threat Hunting and Action Center – ACCESS DEMO A cloud-based SIEM that depends on local Heimdal cybersecurity tools and feeds into an automated response system and also provides a vulnerability manager. Access a free demo.
- Datadog Security Monitoring A Cloud-based monitoring solution with advanced log management. It integrates with +400 built-in tools and services.
- LogRhythm NextGen A leader SIEM platform with advanced AI-based security analytics for threat detection and response.
- IBM QRadar A SIEM platform with a powerful log and traffic flow collection, management, and analytics system.
- McAfee Enterprise Security Manager A popular SIEM for its actionable intelligence, analytics, and threat intelligence.
- Splunk Enterprise Security An analytics-based SIEM and log management solution for machine-generated data.
- AlienVault USM by AT&T Cybersecurity A next-gen SIEM that unifies various capabilities.
- ExaBeam Security Management Platform SaaS-based SIEM platform built with powerful analytics to detect and respond to threats.
- RSA NetWitness Platform Modern SIEM solution with a strong focus on threat detection and response.
What is SIEM?
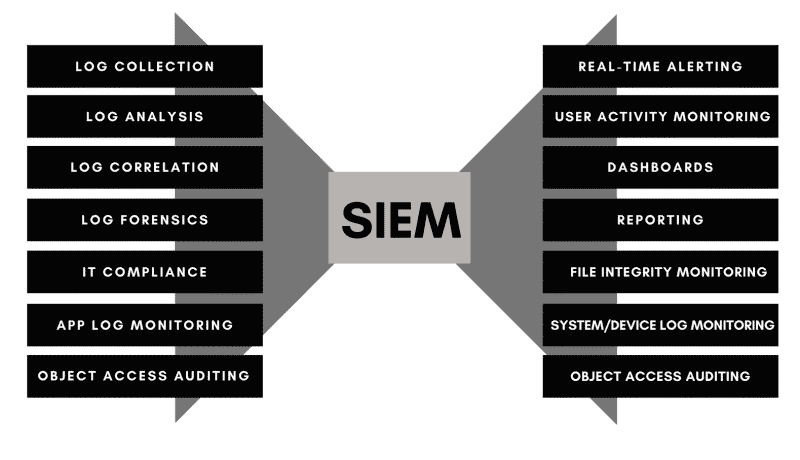
Security Information and Event Management (SIEM) is a general term that covers a wide range of different IT security solutions and practices. In general, SIEM combines the following: Log and Event Management Systems, Security Event Correlation and Normalization, and Analytics.
Other elements found in a SIEM system:
SIEM vs SEM vs SIM
SIEM products and services combine the capabilities of two cybersecurity areas: Security Information Management (SIM) and Security Event Management (SEM).
Although these three concepts (SIEM, SEM, and SIM) are generally used interchangeably, they are not the same. SEM and SIM are both information collection systems that use different methods. SIEM is simply the combination of both.
- SIM: The practice of collecting log data into a central repository and processing it, with correlation and aggregation. SIM collects log data from devices like firewalls, Intrusion Detection Systems (IDS), AntiVirus (AV), routers, switches, proxies, etc.
- SEM: Collects similar data as SIM but looks closer for events (a single log, list of logs, or a record). It centralizes events and provides real-time threat analysis. Examples are suspicious account logins, privilege abuse, and super-user events.
- SIEM? A broader umbrella term (SIM + SEM = SIEM), covering SIM and SEM security tools, practices, and resources.
Why SIEM?
Security systems, such as IDS, IPS, or firewalls provide specialized capabilities that address and target specific threats. For example, an IDS can provide logs limited to the amount and types of attacks, or OS service logs may only provide information on user sessions and configuration changes.
SIEM tools integrate security systems like these, to provide a “bird’s view” of a security incident using real-time monitoring and logs analysis. SIEMs are vital in any cybersecurity strategy because they help detect threats with more efficiency and faster response.

How Does a SIEM Works?
SIEM is not only a specific piece of technology but also a set of practices and principles. To make a SIEM plan work, data must be generated and collected from network devices, databases, endpoints, or security devices. These devices feed their event log and contextual data into a SIEM system which runs critical processes on the data, such as aggregation, correlation, graphics, analysis, etc. Finally, the system outputs results into reports or alerts and in some cases, uses automation for faster response.
- Step 1: Data Collection
SIEM tools usually use a client-side agent installed on security appliances, network devices, domain controllers, firewalls, AVs. The client collects log data and reports back to a central server. - Step 2: Data Normalization and Aggregation
The central station (server) ensures that all data reads the same across all the records. It uses various processes to reduce data redundancy, improve its integrity, and provides a summarized format. A SIEM server combines the data collected from various sources into a summary for data analysis. - Step 3. Data Analysis
The SIEM server uses a statistical model to analyze all received log data and detect threats and anomalies. Modern SIEM tools use more advanced techniques including automation capabilities and behavioral analytics. - Step 4. Alerting
The SIEM tools provide detailed dashboards and alerting systems to ensure security managers are always informed. Alerts may contain anything from critical real-time event information to simple notifications.
SIEM Tools: What to Look For?
Although SIEM tools could vary in terms of scalability, supportability, price, and extra features, they should at least provide a set of essential capabilities and features.
- Log collection and management A SIEM system should be capable of gathering log data to be used for either historical/trend prediction or real-time analysis. Tools that provide a way to manage logs are optimal.
- Data aggregation A SIEM tool should be capable of aggregating and normalizing data. These processes help create a context within a large network by turning data into a standard format.
- Data analysis utilities Take all aggregated data and provide analytics, such as behavioral, diagnostics, predictive, or forensics. Data analysis will help detect threats and vulnerabilities.
- Alerting and notification system Identified threats are classified and alerted based on their severity level.
Additionally, look for more advanced but vital features such as:
- Threat detection and response Identify and manage present threats and provide response capabilities.
- Threat intelligence Use threat intelligence to help identify more sophisticated and difficult-to-spot threats.
- Compliance Reporting Generate reports for data protection compliance and standards.
- Fine-tuning alert and automation conditions Threat response can be automated to improve mitigation time.
Should you go for an on-premises or a cloud-based SIEM?
SIEMs can be expensive and challenging to deploy. Additionally, they often require one or two personnel members for maintenance and monitoring. This is why SIEMs are often more popular among enterprises than in SMBs. However, SIEMs are now becoming more popular across all types and sizes of businesses, this is especially because now, SIEMs can be outsourced to a managed service provider.
Our methodology for selecting the best SIEM tools:
We've broken down our analysis for you based on these key criteria:
- Comprehensive log management and real-time monitoring capabilities.
- Advanced analytics and threat detection techniques.
- Integration with existing security systems and wide compatibility.
- User-friendly interface and efficient incident response features.
- Compliance and reporting features suited for enterprise standards.
The best SIEM tools
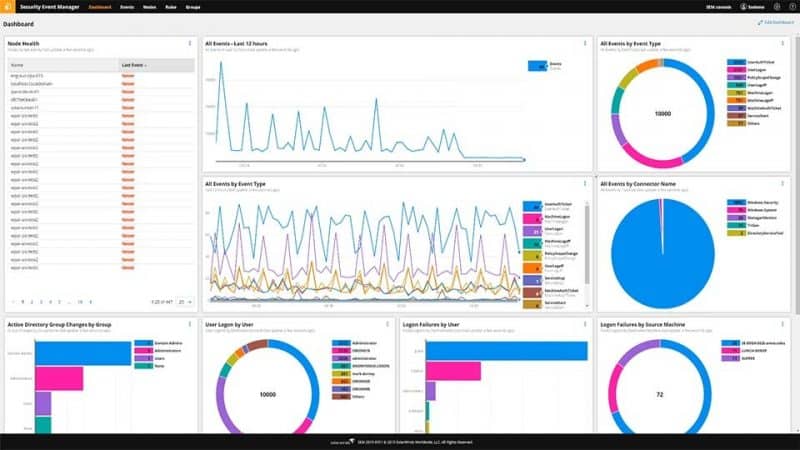
1. SolarWinds Security Event Manager – FREE TRIAL
SolarWinds Security Event Manager (SEM), formerly known as Log & Event Manager, is a SIEM virtual appliance used for monitoring and managing network security. It provides all the core functionalities expected from a SIEM system, including log management, analytics, and real-time monitoring and reporting.
Key Features
- Advanced Correlation: Utilizes a robust engine to aggregate and analyze event logs, enhancing threat detection.
- Real-Time Analysis: Offers immediate threat analysis and response, ensuring timely action against security breaches.
- Integrated Intelligence: Incorporates McAfee Global Threat Intelligence for improved accuracy in threat identification.
- Comprehensive SIEM Suite: Includes a full range of tools for effective security information and event management.
- Active Directory Integration: Seamlessly works with Active Directory, facilitating enhanced network security management.
Why do we recommend SolarWinds Security Event Manager?
SolarWinds Security Event Manager (SEM) is recommended for its comprehensive suite of SIEM functionalities, including efficient log management, sophisticated analytics, and real-time monitoring. It stands out for its advanced alerting and reporting capabilities, making it a robust tool for detecting and managing network security events.
SolarWinds SEM can collect log data from Windows security logs, Windows system and application logs, authentication logs, app-specific logs, and Syslog-enabled devices. It provides access to these logs for troubleshooting, forensics, management, and most importantly for real-time analytics.
Who is it recommended for?
SolarWinds SEM is particularly suited for network and security administrators in enterprise environments who require a powerful, yet user-friendly, SIEM solution. Its range of integrations and simple log filtering options make it a valuable tool for professionals who need to start with little setup or customization.
Pros:
- Efficient Threat Detection: Leverages a powerful correlation engine for quicker identification and mitigation of threats.
- Seamless AD Compatibility: Excellently integrates with Active Directory, making it ideal for complex network infrastructures.
- Designed for Scale: Tailored for large networks, offering solutions that accommodate expansive system requirements.
Cons:
- Pricing Transparency: Requires direct contact with sales for pricing details, lacking upfront cost information.
- Demands Resources: Notably resource-intensive, which could impact system performance in some environments.
Licensing: The price for a perpetual license, starts at $5093.00 one-time and offers a fully functional 30-day free trial. For more information on licensing, get a quote.
EDITOR'S CHOICE
SolarWinds Security Event Manager is our top SIEM tool choice due to its comprehensive log management, advanced analytics, and real-time monitoring capabilities. It stands out in the market for its user-friendly interface, making the complex task of managing network security more manageable.
The integration of a cyber-threat intelligence framework and advanced File Integrity Monitoring system positions it as a highly effective tool for threat detection and response. Additionally, its ability to correlate AV and IDS/IPS event logs enhances its functionality. SolarWinds SEM’s capacity for historical analysis aids in identifying anomalous behavior, crucial for proactive threat mitigation. It’s particularly beneficial for enterprises due to its extensive range of integrations and compliance reporting features.
Download: SolarWinds Security Event Manager - Free Trial
OS: Virtual Appliance (Compatible with Multiple OS)
Download: https://www.solarwinds.com/security-event-manager/registration
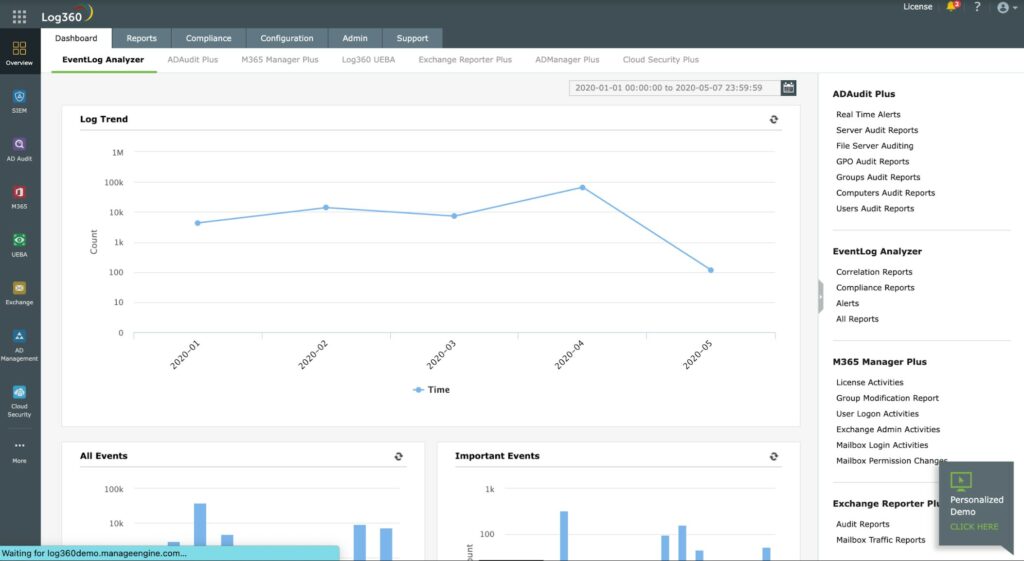
2. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is an on-premises package for Windows Server that collects log messages from your local network and is also able to watch over Active Directory implementations on your site and in the cloud.
Key Features:
- Advanced Log Management: Provides comprehensive log collection and analysis across platforms.
- User Behavior Analytics: Utilizes UEBA to identify deviations from normal activity patterns.
- Automated Response: Orchestrates responses to security incidents, enhancing threat mitigation.
- Real-Time Monitoring: Offers live tracking of system activities for immediate insights.
Why do we recommend it?
ManageEngine Log360 is recommended for its comprehensive log processing capabilities and deployment of user and entity behavior analytics (UEBA). It stands out with its orchestrated responses and live activity metrics, providing robust security monitoring especially for Windows, Linux, and Unix systems. Its integration of multiple threat data streams makes it a versatile choice for network operation centers and managed service providers.
The ManageEngine security methodology deploys user and entity behavior analytics (UEBA) to establish a standard pattern of activity for each user account and endpoint. If behavior deviates from this standard. That user or device is flagged for deeper activity tracking. The UEBA strategy saves time and lightens the processor load from this package.
Who is it recommended for?
This tool is ideal for organizations that need a powerful, cross-platform log management system with a focus on user and entity behavior analytics. It is particularly suitable for environments that require monitoring of Active Directory implementations and those who value robust log analysis and configuration change monitoring.
Pros:
- Visual Dashboards: Features intuitive visualizations, ideal for simplifying data interpretation.
- Threat Integration: Seamlessly incorporates various threat intelligence feeds for enhanced security awareness.
- In-Depth Log Analysis: Facilitates detailed examination of both current and historical log data.
- Cross-Platform Monitoring: Extends monitoring capabilities to Windows, Linux, and Unix systems.
- Configuration Tracking: Helps prevent unauthorized changes and privilege escalations by monitoring system configurations.
Cons:
- Complex Features: The extensive range of features may require a significant amount of time to fully explore and utilize.
- Licensing Complexity: Pricing is determined by numerous factors, necessitating a personalized quote for accurate cost assessment.
Licensing: The price for Log360 is assembled from many different factors, so you need to request a quote to get the price for your implementation.
Download: Get a 30-day free trial of ManageEngine Log360.
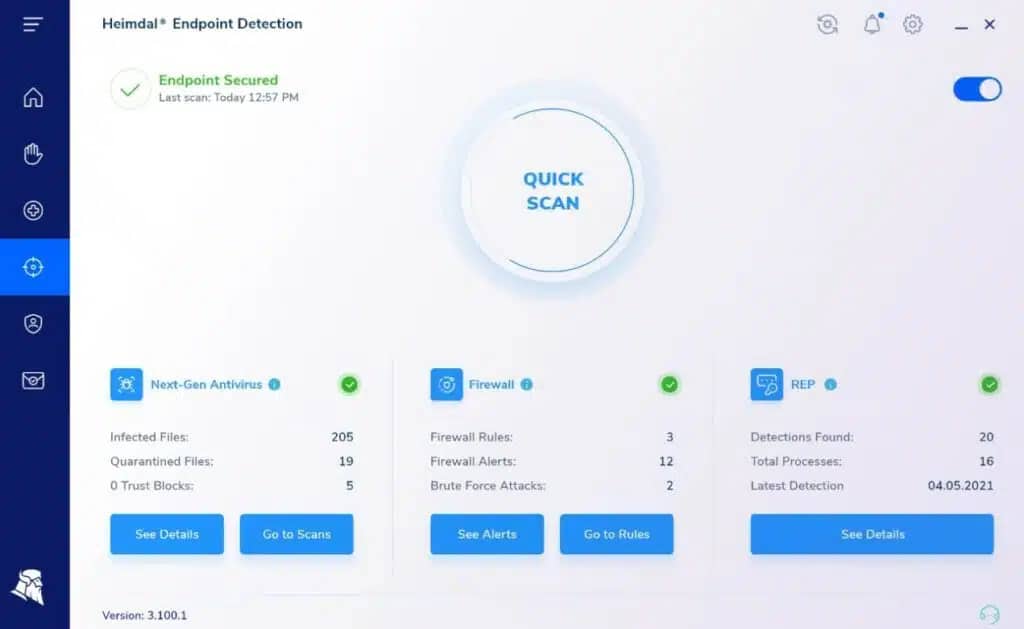
3. Heimdal Threat Hunting and Action Center – ACCESS FREE DEMO
Heimdal Threat Hunting and Action Center provides a SIEM and an automated response service that adds onto Heimdal products designed to run on-site. The cloud-based system performs threat detection on data uploaded by those local Heimdal cybersecurity tools.
Key Features
- Hybrid Security: Creates a cohesive security system by integrating with Heimdal's suite of tools.
- Automated Responses: Links threat detection with automatic countermeasures for efficient threat mitigation.
- Vulnerability Scanning: Includes comprehensive scanning to identify and alert on system vulnerabilities.
Why do we recommend it?
Heimdal's Threat Hunting and Action Center is recommended for its unique hybrid security system that works in tandem with Heimdal tools. It offers automated response capabilities and includes vulnerability scanning, enhancing overall network security. The platform's ability to scan for vulnerabilities and provide alerts for all endpoints when one is attacked makes it a proactive tool in threat management.
The SIEM requires three different Heimdal tools to be operating on a protected site. One of these must be the Next-Generation Anti-Virus, which runs on Windows, macOS, and Linux and incorporates a mobile device management system for Android and iOS devices. The other tool tools can be selected from Network Security, Email Security, Patching & Asset Management, or Endpoint Security.
Who is it recommended for?
Recommended for businesses using Heimdal cybersecurity tools, as it integrates well with them. It is ideal for organizations looking for a SIEM solution that offers a company-wide perspective and automated threat shutdown capabilities.
Pros:
- Company-Wide Perspective: Offers a global view of security threats, enhancing overall protection.
- Proactive Threat Management: Identifies and neutralizes threats automatically, ensuring swift response times.
- Endpoint Vulnerability Alerts: Alerts all endpoints if a vulnerability is detected, bolstering network defense.
- Insider Threat Detection: Monitors for signs of insider threats, unauthorized access, and data theft, maintaining data integrity.
Cons:
- No Trial Available: Lacks a free trial option, limiting preliminary evaluation opportunities.
- Licensing Details: Pricing information is not publicly disclosed, requiring direct inquiry for details.
Licensing: Heimdal doesn’t publish a price list
Demo: Access a demo of the Heimdal Threat Hunting and Action Center service
4. Datadog Security Monitoring
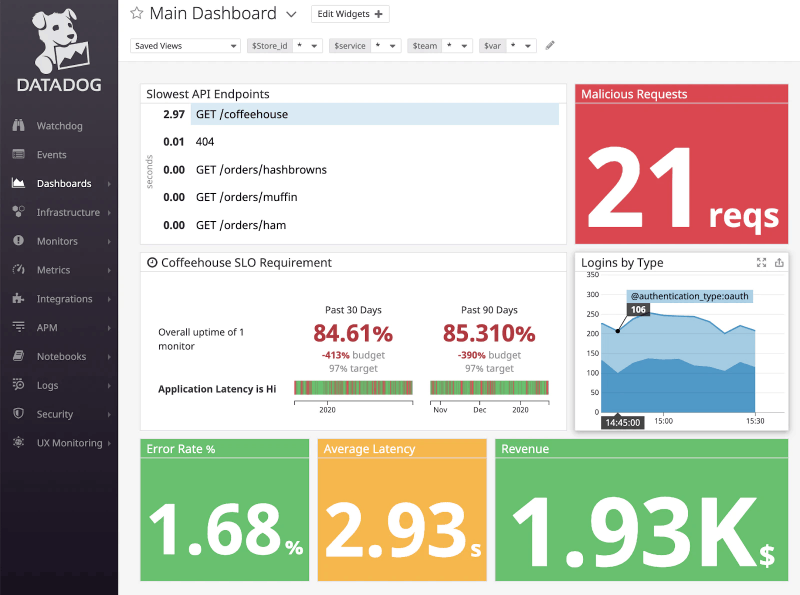
Datadog is a cloud-based monitoring service for applications, servers, databases, tools, and services. It can collect metrics, traces, logs, and live events. It uses its SaaS-based data analytics platform to analyze collected data and detect anomalies.
Key Features
- Real-Time Security: Offers immediate monitoring and alerting on security threats across the network.
- Centralized Data Management: Aggregates logs, metrics, and traces for unified management and analysis.
- Extensive Integration: Supports over 400 built-in tools and services for comprehensive monitoring coverage.
- Advanced Alerts: Features a sophisticated alerting system to notify of potential security incidents promptly.
Why do we recommend it?
Datadog Security Monitoring is recommended for its cloud-based, real-time security monitoring and centralized management for logs, metrics, and traces. Its ability to integrate with over 400 built-in tools and services, along with an advanced alert and notification system, makes it a comprehensive choice for diverse IT environments.
Datadog uses lightweight agents to collect and aggregate all this data (from more than 400 different technologies) into a central server, and present data in a dashboard. The Datadog server provides a security monitoring module that analyzes all logs and live-event data and alerts if it detects abnormal activity.
Who is it recommended for?
This tool is suitable for businesses of various sizes that require scalable monitoring solutions. It is particularly beneficial for those who need both internal and external network monitoring, and for organizations that value flexibility in pricing options.
Pros:
- Comprehensive Data Collection: Facilitates detailed security analysis through live log and event data collection.
- Internal and External Monitoring: Provides a holistic view of network performance and security, inside and out.
- Scalable Monitoring: Allows for flexible, scalable monitoring solutions to fit business needs and budget constraints.
Cons:
- Trial Period: A longer trial period would be beneficial for more thorough testing and evaluation.
Licensing: Datadog offers a wide range of plans to suit your needs. For example, for Log Management, the price starts at $ 0.10/ingested or scanned GB /month. For more pricing information, check Datadog’s website.
Get a free trial of Datadog for 14 days.
5. LogRhythm NextGen
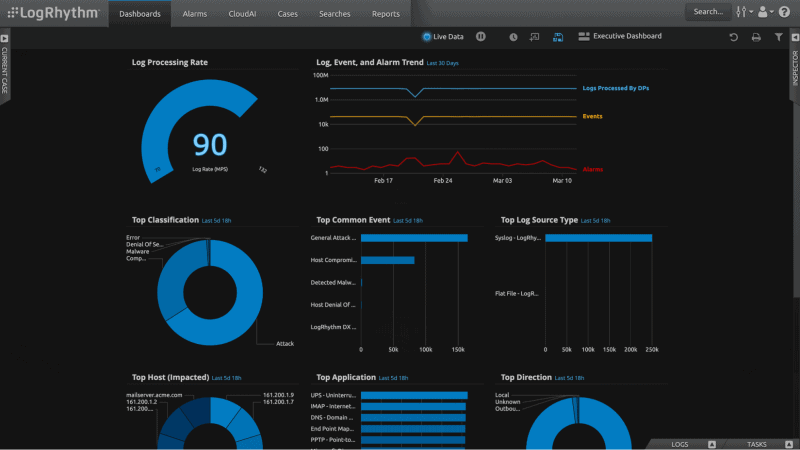
LogRhythm is a cyber-security intelligence company that has positioned itself as one of the leaders in SIEM, log management, network and endpoint monitoring, forensics, and security analytics software. LogRhythm NextGen is their SIEM platform that provides advanced AI-based security analytics for threat detection and response.
Key Features
- Advanced Analytics: Leverages AI for sophisticated security analytics, enhancing threat detection.
- Security Posture Assessment: Utilizes the Security Operations Maturity Model to evaluate security practices.
- Cloud Data Integration: Open Collector technology enables efficient cloud data sourcing.
- Compliance Readiness: Features pre-built modules for various compliance standards.
- Threat Intelligence: Integrates global threat intelligence for a comprehensive security overview.
Why do we recommend it?
LogRhythm NextGen is recommended for its advanced AI-based security analytics, which are key in threat detection and response. The integration of UEBA, NTA, and SOAR in one platform, combined with its Security Operations Maturity Model, makes it a leader in SIEM technology.
The platform collects, normalizes, and aggregates log data from different devices. It used the data to provide real-time monitoring and intelligent incident response. LogRhythm is popular because it integrates security analytics with User Entity Behavior Analytics (UEBA), Network Traffic Analysis (NTA), and Security Orchestration Automation and Response (SOAR), all in a single central place.
Who is it recommended for?
Ideal for organizations seeking a beginner-friendly SIEM tool with a sleek interface and customizable options. It's well-suited for those who require a mix of log management, compliance modules, and advanced threat intelligence in one solution.
Pros:
- Beginner-Friendly: Simplifies security tasks with user-friendly wizards, making it accessible to beginners.
- Customizable Interface: Offers a sleek, highly customizable dashboard for a better user experience.
- AI-Driven Analysis: Employs AI and machine learning for effective behavior analysis and anomaly detection.
Cons:
- Trial Availability: Lacks a readily available trial option for preliminary assessment.
- Platform Support: Expansion into cross-platform support would enhance its versatility.
Licensing: LogRhythm offers three plans: Software Solution, True Unlimited Data Plan, and High-Performance Appliance.
Request LogRhythm NextGen’s custom free demo.
6. IBM QRadar
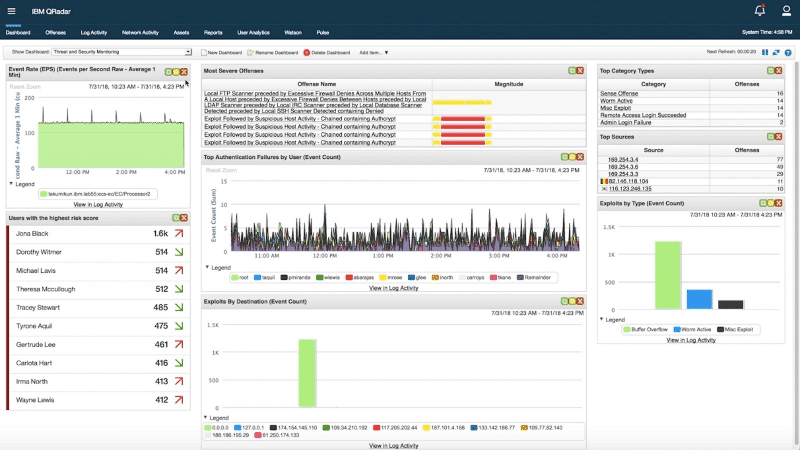
IBM QRadar is a powerful SIEM platform that, for a long time, has managed to secure a top position in the SIEM tools market. The tool provides all basic SIEM functionalities including log management, data collection, aggregation, and analytics.
Key Features
- Real-Time Data Storage: Captures and stores network data in real-time, ensuring timely threat detection.
- Analytical UI: Provides an insightful user interface with graphs, reports, and alerts for comprehensive analysis.
- Data Handling: Excels in data parsing and normalization for accurate security insights.
- Integrated Security Suite: Seamlessly integrates with QRadar's extended security management tools.
Why do we recommend it?
IBM QRadar is recommended for its powerful data collection, parsing, and normalization capabilities. The real-time network data storage and comprehensive user interface with robust analytics tools make it a top choice in the SIEM market.
The IBM QRadar collects logs and traffic flows and uses QRadar Log Manager for all log management functions. It processes, aggregates, and stores all this data into the QRadar platform. The platform then provides real-time visibility so you can detect, prioritize and alert threats.
Who is it recommended for?
It is particularly suited for organizations that require a Linux-based SIEM solution with advanced AI capabilities for risk assessment and threat prioritization.
Pros:
- AI-Powered Risk Assessment: Utilizes AI for in-depth risk analysis and network impact simulations.
- Intuitive Interface: Features a straightforward, effective dashboard for easy operation.
Cons:
- Platform Specificity: Primarily available for Linux, limiting its application in non-Linux environments.
- Integration Capabilities: Could benefit from enhanced integration with other security platforms.
Licensing: Contact for pricing information.
Register for a 14-day free trial of IBM QRadar.
7. McAfee Enterprise Security Manager
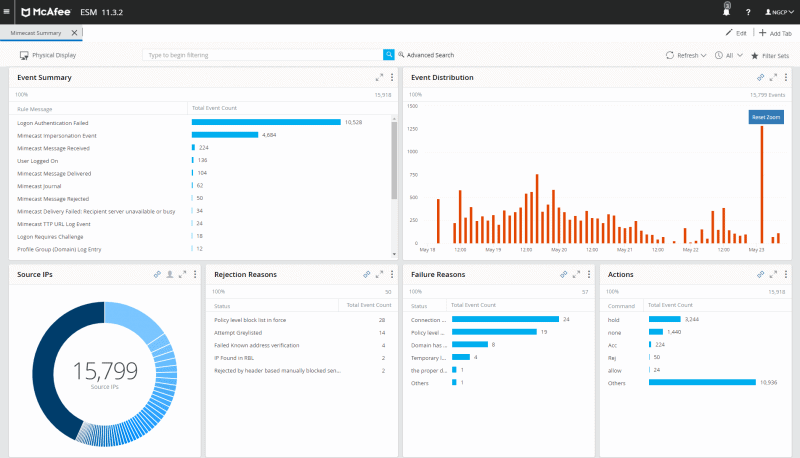
McAfee Enterprise Security Manager (ESM) is a well-known SIEM solution, popular for its actionable intelligence and advanced analytics. As a SIEM, McAfee SEM can collect logs from a wide range of sources, correlate all event logs (including real-time and records), and provide real-time analysis and threat response.
SIEM includes:
McAfee Advanced Correlation Engine
McAfee Application Data Monitor
McAfee Enterprise Log Manager
McAfee Enterprise Log Search
McAfee Enterprise Security Manager
McAfee Global Threat Intelligence (GTI) for ESM
Key Features:
- Comprehensive Log Collection: Gathers logs from a multitude of sources for in-depth analysis.
- Real-Time Threat Analysis: Offers immediate analysis and response to security threats.
- Advanced Correlation Engine: Employs a sophisticated engine to correlate event logs for accurate threat detection.
- Global Threat Insights: Integrates McAfee's Global Threat Intelligence for enhanced threat anticipation.
Why do we recommend it?
McAfee Enterprise Security Manager is recommended for its powerful correlation engine and actionable intelligence, making it effective in eliminating threats swiftly. Its integration with Advanced Threat Intelligence and various McAfee tools enhances its capability in large network environments.
The McAfee ESM provides a correlation engine to aggregate, normalize and analyze all collected event logs and alert when there is a threat. The dashboard shows all activity in real-time and provides actionable intelligence to remediate and respond to threats. The system uses its Advanced Threat Intelligence to identify threats faster and with more precision.
Who is it recommended for?
This tool is ideal for large organizations with complex network environments, especially those that require a strong focus on Active Directory integration and advanced analytics.
Pros:
- Efficient Threat Elimination: Utilizes a powerful correlation engine for swift threat identification and resolution.
- Active Directory Synergy: Excels in environments requiring strong Active Directory integration.
- Scalability: Designed to cater to the complex needs of large network infrastructures.
Cons:
- Pricing Transparency: Requires contacting sales to obtain pricing, lacking immediate clarity on costs.
- Resource Intensity: Demands significant system resources, which may impact performance in constrained environments.
Licensing: Contact McAfee for a price quote.
Trial: McAfee offers a free trial for ESM.
8. Splunk Enterprise Security
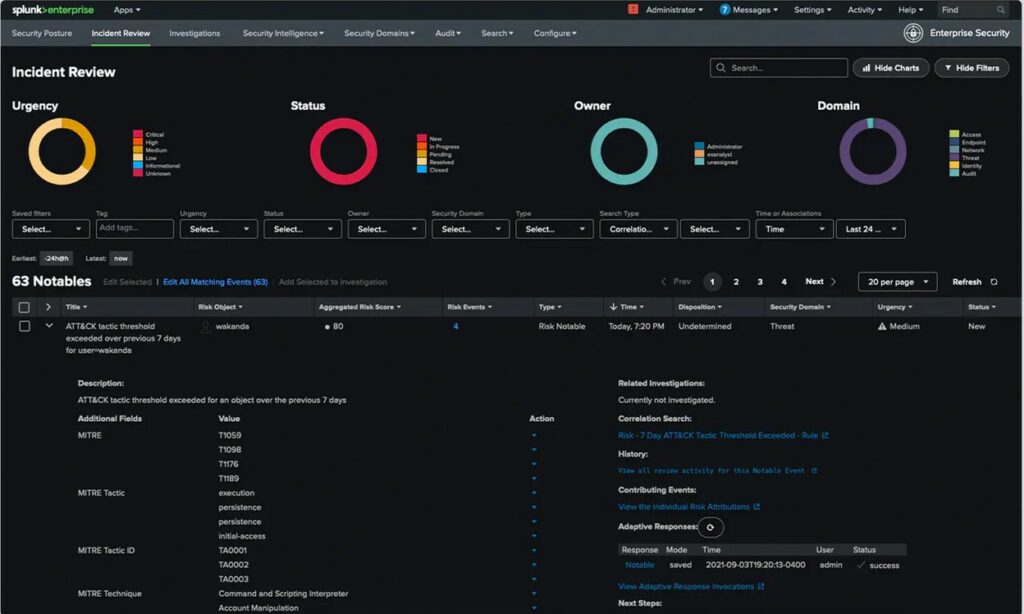
Splunk is a leading developer of web-based software for searching, monitoring, and analyzing machine-generated data. It provides outstanding security via its SIEM, AIOPs, ML, Application and log management, and IT compliance software.
Key Features
- Automated Data Integration: Streamlines data collection automatically for efficiency.
- Rule-Based Correlation: Utilizes predefined rules to correlate data, enhancing threat detection.
- Advanced Threat Insights: Employs analytics to identify sophisticated threats beyond log data.
- Interactive Dashboards: Offers dynamic alerts, reports, and dashboards for real-time insights.
- Guided Decision Making: Provides workflow-based content to assist in decision-making processes.
Why do we recommend it?
Splunk Enterprise Security is recommended for its behavior analytics and ability to detect advanced threats not visible through logs. Its high customization and visual interface make it an excellent choice for creating operational and business intelligence from data.
Splunk Enterprise Security (ES) is a full analytics-driven SIEM solution. It uses behavior analytics, actionable intelligence, and automation to monitor and protect enterprises from modern threats. Splunk ES can be deployed on the cloud, SaaS, on-premises, or (hybrid) through a combination of all.
Who is it recommended for?
This solution is best suited for large enterprises that require a comprehensive analytics-driven SIEM solution, capable of deployment in various environments including cloud, SaaS, and on-premises.
Pros:
- Behavioral Threat Detection: Excels in uncovering hidden threats through behavior analysis, not just logs.
- Intuitive Interface: Features a highly visual and customizable user interface for superior data visualization.
- Event Prioritization: Simplifies the process of prioritizing security events for faster response.
- Operational Intelligence: Converts data into operational and business intelligence, empowering strategic decisions.
- Cross-Platform Availability: Supports both Linux and Windows environments, offering versatile deployment options.
Cons:
- Enterprise Focus: Primarily tailored for large enterprises, possibly limiting its appeal for smaller organizations.
Licensing: Contact Spunk for pricing information.
Sign in for an interactive Splunk Enterprise Security demo, or try a free trial.
9. AlienVault USM by AT&T Cybersecurity
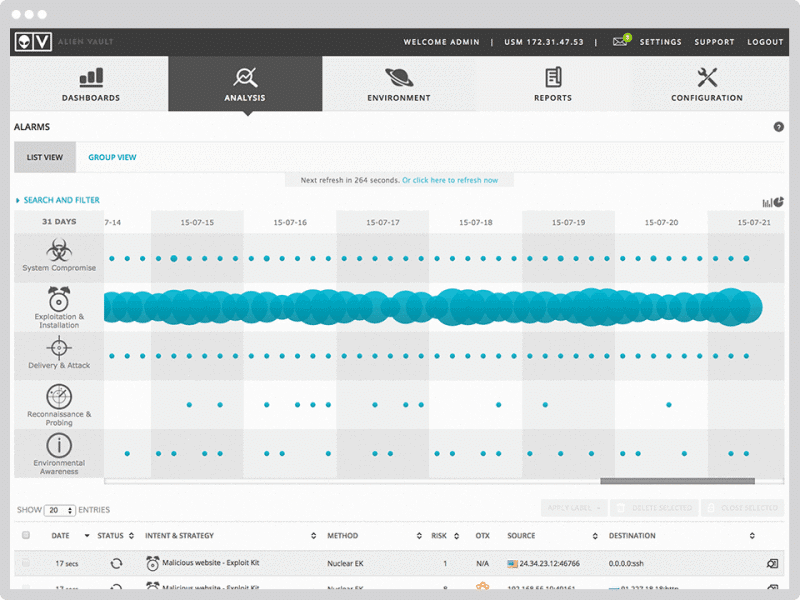
AT&T CyberSecurit’s AlienVault Unified Security Management (USM) platform was built out of the necessity to overcome certain limitations of current SIEM systems. Gartner recognized AlienVault in 2016 as the only “Visionary” vendor attempting to change the way threat detection and incident response were done.
Key Features:
- Integrated Threat Intelligence: Combines AlienVault Labs and Open Threat Exchange for enriched threat data.
- Comprehensive Threat Detection: Features advanced network and host intrusion detection systems.
- Unified Security Management: Centralizes data collection, normalization, and correlation for streamlined threat management.
- Actionable Alarms: Delivers alarms and actionable intelligence for effective incident response.
Why do we recommend it?
AlienVault USM is recommended for its unified approach to threat management, detection, and response. Its integration of Asset Discovery, Vulnerability Assessment, Threat Detection, Behavioral Analysis, and Security Intelligence makes it a visionary tool in the SIEM landscape.
AlienVault USM, at its core, is a SIEM system but evolved into a USM, and focused on providing centralized threat management, detection, and response. The platform is composed of five integrated or “unified” capabilities including Asset Discovery, Vulnerability Assessment, Threat Detection, Behavioral Analysis, and Security Intelligence.
Who is it recommended for?
It is ideal for businesses that require a comprehensive SIEM system with capabilities for scanning log files, vulnerability assessment, and shared threat intelligence, and that value AI assistance in threat detection.
Pros:
- Versatile Platform: Supports both Mac and Windows, accommodating a wide range of IT environments.
- Enhanced Vulnerability Assessment: Provides detailed vulnerability reports by scanning network devices and applications.
- Community-Driven Intelligence: Benefits from a user-powered portal for sharing and improving threat data collectively.
- AI-Assisted Threat Hunting: Utilizes artificial intelligence to support administrators in identifying and mitigating threats.
Cons:
- Trial Limitations: A longer trial period would offer a more thorough evaluation experience.
- Integration Flexibility: Additional integration capabilities with other security systems would enhance its utility.
Licensing: AlienVault USM is available in three different editions, Essentials ($1075/month), Standard ($1695/month), and Premium ($2595/month).
Download AlienVault USM free trial for 14 days.
10. ExaBeam Security Management Platform
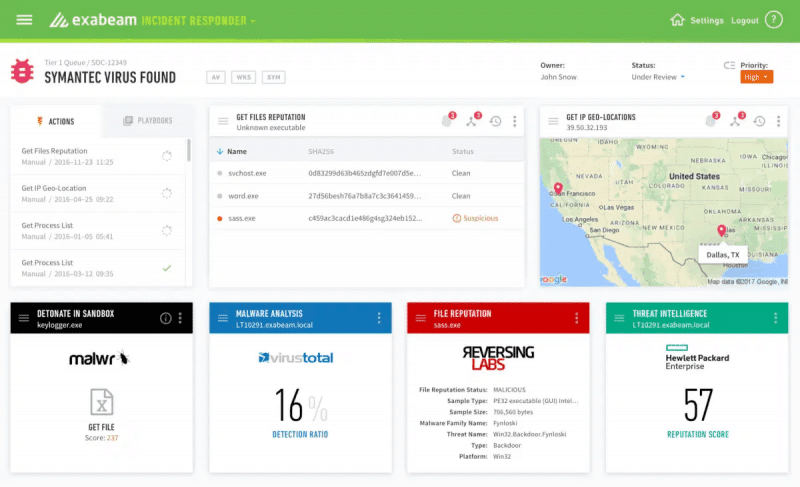
The ExaBeam Security Management Platform is a SaaS-based SIEM solution built with powerful analytics to detect abnormal users and threats. It also comes with automation capabilities to improve detection and response time.
Key Features
- Extensive Log Management: Offers comprehensive management of log data across systems.
- Behavior Analytics Integration: Integrates with UEBA for nuanced user and entity behavior insights.
- SOAR Capabilities: Features the Incident Responder module for streamlined security operations.
- Analytical Proficiency: Applies analytics with correlation rules and attack signatures for precise threat detection.
- Machine Learning Detection: Automates threat detection with advanced machine learning techniques.
Why do we recommend it?
ExaBeam Security Management Platform is recommended for its comprehensive log management and integration with UEBA and SOAR capabilities. Its focus on automated detection via machine learning makes it a strong contender in the SaaS-based SIEM market.
The ExaBeam Security Management Platform provides more than 350 integrations for different data sources. It collects data from inbound sources and correlates all necessary security events and logs from the sources. The platform can also integrate outbound systems to automate incident response, such as alerts or reports.
Who is it recommended for?
This platform is particularly suitable for organizations that need advanced incident response workflows, extensive data querying features, and compliance reporting capabilities, but don't require live network monitoring.
Pros:
- Incident Response Efficiency: Enhances incident response with workflows, playbooks, and automation.
- Powerful Data Querying: Provides robust query features for effective filtering of vast data sets.
- Compliance Assistance: Facilitates compliance reporting and audits for standards like HIPAA and PCI DSS.
Cons:
- Network Monitoring Gap: Does not include live network monitoring, limiting real-time threat visibility.
- Original Design: Initially not conceived as a SIEM tool, which may affect its foundational approach to security management.
Licensing and Pricing: Get a quote.
Register for a free demo.
11. RSA NetWitness Platform
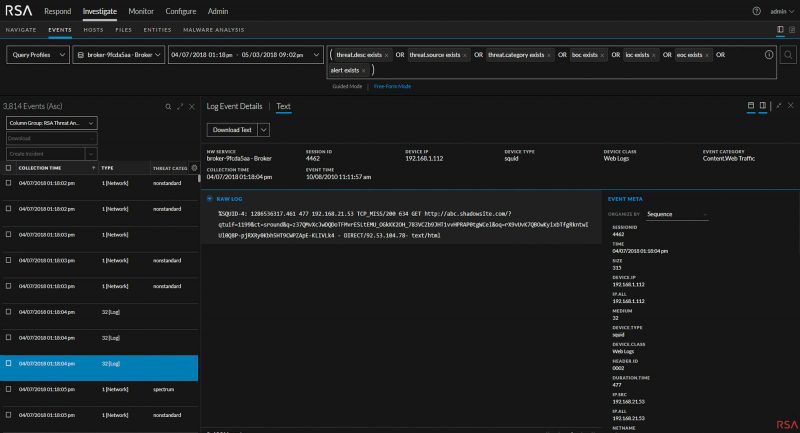
The RSA NetWitness Platform is an innovative SIEM solution with a strong focus on threat detection and response. It is armed with security orchestration and automation to improve the precision of threat detection and response time.
Key Features:
- Customizable Dashboard: Tailor the interface to meet the specific monitoring needs of your organization.
- Advanced Detection Capabilities: Utilizes network and endpoint detection for a comprehensive security overview.
- Real-Time Threat Investigation: Implements live queries and filters for dynamic threat analysis.
- Efficient Logs Management: Organizes and maintains logs effectively for improved data retrieval.
- Automated Remediation: Features guided and automated processes to address security issues swiftly.
- Pre-Configured Reporting: Includes out-of-the-box reports to streamline compliance and monitoring.
Why do we recommend it?
RSA NetWitness Platform is recommended for its flexibility and strong focus on threat detection and response, backed by security orchestration and automation. Its customizable dashboard and advanced threat investigation tools make it a comprehensive solution for enterprise networks.
The RSA NetWitness Platform can ingest a wide variety of data from logs, events, to packets from different sources. Then, it aggregates and correlates this data to create metadata that can be used to search through and query. The platform also uses UEBA to compare the contextualized data to threat intelligence and correlation rules to identify suspicious behaviors.
Who is it recommended for?
Ideal for large organizations that need a cloud-based solution with a simple interface, capable of leveraging extensive intelligence networks for threat identification and prevention.
Pros:
- Cloud Flexibility: Offers a cloud-based solution adaptable to various enterprise environments.
- Intuitive Interface: Features a user-friendly dashboard that simplifies complex data analysis.
- Extensive Threat Intelligence: Integrates vast intelligence networks for enhanced threat detection and prevention.
- Enterprise-Ready: Specifically designed to support the complex security demands of large organizations.
Cons:
- Limited Accessibility: No free trial available, which may limit initial evaluation by potential users.
- Opaque Pricing: Requires direct contact for pricing information, complicating budget planning for interested parties.
Licensing and Pricing? Contact sales.
Request an RSA NetWitness Platform demo.