When attempting to transfer files using the SFTP protocol, you get the message “Received message too long… ” in your Linux or macOS machine. Your Windows machine shows something similar: “Received too large (some number) SFTP packet”, “Max supported packet size is …”. The message means that the SFTP client received bad or unknown data from the SFTP server.
The primary cause and solution to the “SFTP Received message too long” error?
- Causes When the SFTP server is using a shell other than the default. A printed output on the terminal shell is polluting the normal SFTP message flow.
- Solution Disable this printed output on the shell or change to the default or appropriate profile or shell. But, again, the answer is on the server and not on the client.
To learn more, keep reading.
Here is our list of the best alternatives to OpenSSH:
- Serv-U Managed File Transfer Server (EDITOR'S CHOICE) – Reliable FTP server for securely transferring files from web and mobile devices.
- Bitvise SSH Server – Secure remote access software based on SSH. It is a client-server architecture that provides a secure channel for communicating over insecure networks.
- Syncplify.me SFTP Server – Dependable cross-platform FTPS and SFTP server known for its extensive security.
The Error: SFTP Received Message Too Long
The following message appears when trying to access an SFTP server from a Linux-based SFTP client.
The “Received message too long” looks like this on a Linux machine:
# sftp user001@ftp.itt.com
|
The “Received too large SFTP package” looks like this on a Windows PC:
Received too large (1433299822 B) SFTP package. Max supported package size
|
Technical Background
SFTP (and SCP2) are file transfer protocols based on the SSH process— they use the SSH session to “speak.” SFTP and SCP2 are non-interactive protocols (non TTY). So any unique code on the server designed to output a message on an interactive login shell (SSH) will produce an SFTP or SCP error. For smooth and clear communication, either end (client and server) must only transmit relevant information on the actual protocol used at that moment (either SFTP or SCP).
The “SFTP received message too long” error is due to an “unclean” SSH session established by the SFTP server-side for various reasons like:
- The SFTP server uses shell startup file scripts like .bashrc or .profile, which could be displaying output (printing data in the terminal) such as MOTD or welcome messages targeted to end-users logging into the server.
- The shell startup is also often used to run personalized scripts that trigger a customized terminal setup, such as restricting a remote user (and using a message).
- Debugging “echo” statements that might be popping after each successful login.
Refer to the below SSH message flow:

The SFTP client might be authenticating successfully, but once it tries to establish an SSH session over the startup shell, the server inserts these output text messages into the SFTP stream—and contaminates the message flow. This is why you should be able to SSH into the server, but not SFTP and SCP.
When the SFTP client receives this “strange” output from the SFTP server, it attempts to parse it as intended (as a standard SFTP message). But the client cannot interpret this message (which is more significant than usual), so it returns a “received message too long”.
Reading the Message Output
The decimal value returned by the SFTP server on the error message has a meaning. It represents an ASCII value that can help you understand what the SFTP (or SCP) server is trying to say.
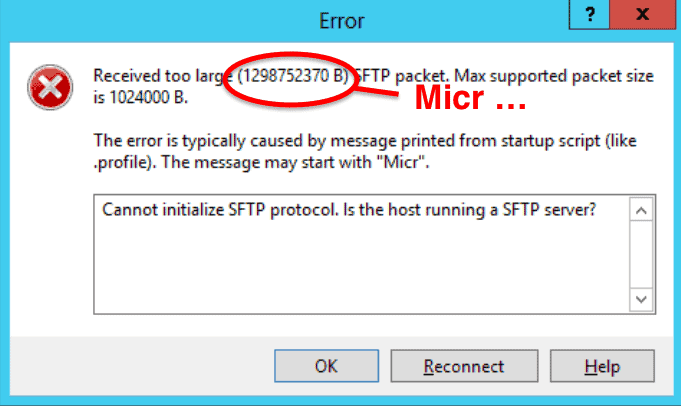
For example, the above error display is from Windows Secure Copy (WinSCP) Windows (Microsoft) program. The message shows the field “Micr,” a 32-bit message sent from the shell terminal.
How to translate this number
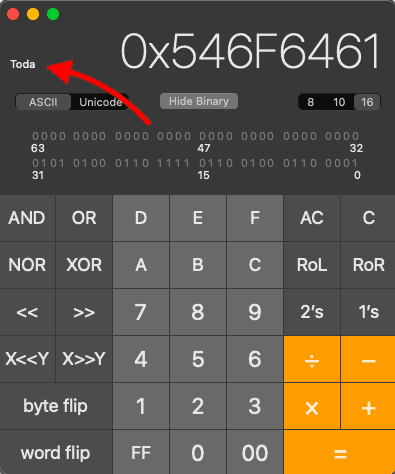
Fire up your programmer calculator and convert from Dec > Hex > ASCII. For instance:
- 1416586337 decimal = 546F6461 hex = “Toda” in ASCII
- 1296449824 decimal = 4D464120 hex = “MFA” in ASCII
- 707406373 decimal = 2A2A2A25 hex = “***%” in ASCII
This will not solve your problem, but it will help you locate the statement causing the problem from the server’s side.
Once you know your keyword, for instance, “MFA” or “Toda”, you may have a clue. MFA, for example, could be due to a script using MFA to authenticate users via a message like “MFA verification code:”. Or another example, “Toda,” which stands for Today— a common MOTD statement.
Troubleshooting the SFTP Received Message Too Long
Solution 1. Test your access and use different users
In some cases, the bash login might send messages like “Please login as the user “admin” rather than the user “root” over the SSH terminal, resulting in the same “SFTP received message too long“. A quick workaround is using the correct user with the right profile.
From the server:
- If you need to use the root user, allocate the right profile script. The server’s root account may have incorrect profile scripts. There are different profile scripts for the terminal (TTY allocated) and non-terminal sessions (non-TTY). The messages are supposed to be printed only from the script of terminal sessions (SSH).
- Consider if the problem is happening to all SFTP or a singular user. If it is a problem for everybody, then check the system-wide startup shell found in /etc. However, if the problem is for a singular user, find their shell file within their home directory. Then, move such scripts generating output from the .bashrc to the user’s .bash_profile, which only runs when you initialize them with a physical shell session.
Solution 2: Comment out the polluting messages
Look for debug statements or conditional scripts that generate output from /etc/bashrc or /etc/profile.
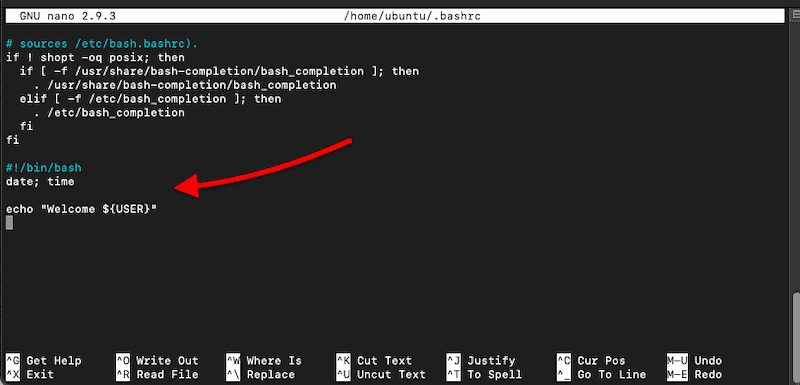
- Open the startup shell script, bashrc, or profile.
- Use nano ~/.bashrc (or your favorite text editor).
- Open the startup shell files (.bashrc) with the vi or nano editor.
- Locate debug statements, welcome messages, or echo commands such as the ones below and comment on them (#). Or change them to avoid running during the non-interactive SFTP (SSH) session.
Solution 3: Isolate the SFTP Session
You may also want to run your custom shell startup file while still allowing SFTP to go through.
To do this, you’ll need to configure your server to use the internal SFTP server directive so the end-user doesn’t use the standard shell to establish an SFTP connection.
- Find and open the SSH config file with a text editor (vi or nano). This file is usually under /etc/ssh/sshd_config.
- Locate and comment the line: Subsystem sftp /usr/lib/openssh/sftp-server
- Add the new line: Subsystem sftp internal-sftp
- Restart the service: sudo service sshd restart
Solution 4: Advanced
Rather than commenting or removing a statement from the bash startup file, you can also configure the shell script for an early exit from SFTP, but keep reading the script.
An example of an early exit
if sftp -q $remote $local
|
Try Alternatives to OpenSSH
The Linux-based SFTP server is likely using OpenSSH, an open-source collection of secure network utilities based on the SSH protocol. OpenSSH is the leading solution for running SSH on Linux distributions. It is accessible and highly versatile but requires advanced expertise and management.
Using a complete and feature-rich client/server SFTP solution will help minimize the chances of clients facing the “sftp received message too long”
Our methodology for selecting the best alternative to OpenSSH:
We reviewed the market for OpenSSH alternatives and analyzed tools based on the following criteria:
- Security mechanisms during file transfer to protect data integrity and privacy
- Support for transferring large files
- Integrations with different applications, including custom ones
- Support for multiple transfer protocols
- Automation features
The Best Alternatives to OpenSSH
Below are three solutions that provide SFTP server/client for Windows and Linux. All solutions also offer a great degree of access control, and one even includes a scripting framework for customizing your SFTP server.
1. Serv-U Managed File Transfer Server – FREE TRIAL
The Serv-U Managed File Transfer Server is a versatile and robust FTP solution. It supports a wide range of secure file-sharing options including, SFTP, FTPS, FTP, and HTTP/S, over IPv4 or IPv6 networks. In addition, this software lets you remotely set up new domains, add users/groups, keep track of FTP sessions and logs, and most importantly, define access permissions.
Key Features:
- Secure File Sharing: Built-in security features for safe sharing, password protect files, and even set them to automatically expire and be deleted after a certain time. Also, it offers
- Automatic IP Lockouts: Prevents cyberattacks, especially brute-force attacks
- Automated Transfers: Streamlines workflows with event-based automated file transfer actions, saving many hours of time and effort.
- Easily Control Configurations: Server domains, users, and group events to trigger actions, without requiring extensive coding.
- Integrations: Integrates well with many third-party applications and shared databases, also seamlessly blends with intranet, web portal, or any custom application.
Feature Distinction
What makes this tool unique is its ability to support the transfer of large files and ad hoc sharing with those within and outside an organization.
Why do we recommend it?
The Serv-U Managed File Transfer Server is a reliable tool that allows your employees to send and receive files securely from anywhere, including from mobile devices. Its centralized management provides complete visibility to administrators and ensures compliance with leading regulations.
As an administrator, you can set up limitations and permissions for the FTP operations and file shares. You can set permissions for file-sharing defined at the user, group, or domain level.
Who is it recommended for?
A good choice for network administrators of large organizations who want to have complete control and security over the file transfers within their organization.
Pros:
- Works well on web and mobile devices
- Transfers large files
- Offers automation capabilities
- Supports FIPS 140-2 cryptography
Cons:
- Configuration settings can be more intuitive
- Active Directory integration can be confusing
Serv-U MFT Server is deployable on-premises. It installs on Windows or Linux platforms. Click here for a fully functional 14-day free trial.
EDITOR'S CHOICE
Serv-U Managed File Transfer Server is our editor's choice because it enables secure file sharing, within and outside your organization. It also supports the transfer of files, regardless of their size. Moreover, it supports multiple protocols like FTP, FTPS, SFTP, HTTP, and HTTPS. Above everything, it is easy to install and use and requires no additional software.
Download: Download a 14-Day Free Trial
Official Site: https://www.solarwinds.com/serv-u-managed-file-transfer-server
OS: Windows, Linux
2. Bitvise SSH Server
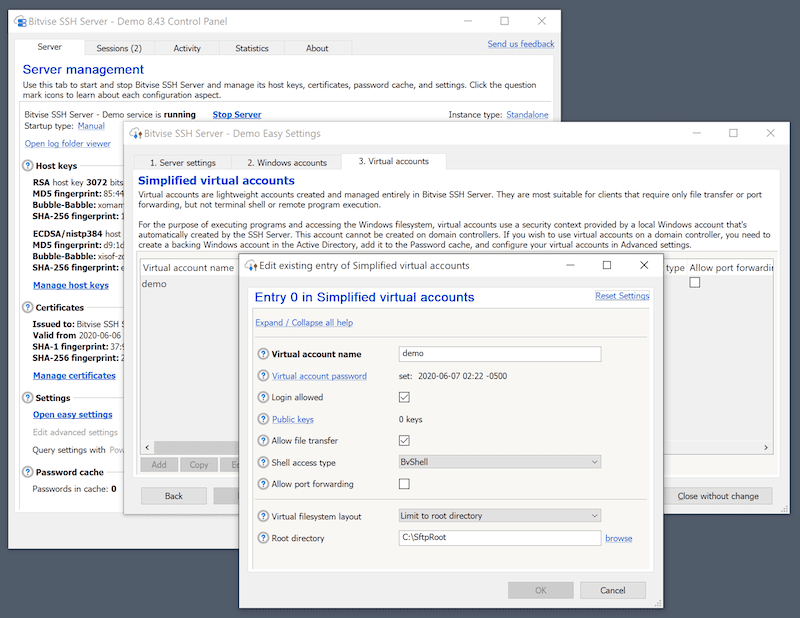
Bitvise is an SSH server solution (Bitvise SSH Server and SSH Client) for Windows environments (a great alternative to OpenSSH). The software includes secure file transfer (over SFTP, SCP, SSH, and even FTPS), terminal shell, and tunneling. In addition, the SFTP and SCP server supports a wide range of different clients.
Key Features:
- Flexible Interfaces: Offers both a GUI and a command-line interface to suit the preferences of different audiences across a wide range of scenarios.
- Remote Access: Remotely access all desktop and server versions of Windows, offering flexibility through a tool called WinVNC, a desktop-sharing system that uses the Remote Frame Buffer (RFB) protocol.
- Multiple Protocols: Supports different transfer protocols like SFTP, SSH, SCP, and VPN through the TCP/IP tunneling feature. This versatility makes this tool ideal for transferring files across different industries.
Why do we recommend it?
We highly recommend Bitvise because security is a central feature of this platform, as it encrypts data during transmission.
Bitvise SSH Server is designed for Windows. As soon as it is installed, it will work immediately without additional configuration. From there, you can restrict or allow access to different user accounts and features. For example, the transfer clients can be limited to single or multiple directories. In addition, the terminal shell clients can be restricted to the same virtual filesystem only by pointing to the shell access type.
Who is it recommended for?
This tool is best suited for administrators who often perform remote troubleshooting on Windows devices.
Pros:
- Easy to install and use
- Supports many transfer protocols
- Integrates with many tools
- Command-line and GUI interfaces
Cons:
- Works best on Windows only
- Free version is available for only a limited time
Bitvise SSH Server is available to download for a fully functional 30-day trial. But you can also choose the limited Bitvise SSH server personal edition free of charge.
3. Syncplify.me SFTP Server
Syncplify.me is a secure and robust FTPS and FTPS server for 64-bit Windows environments. The server can automatically detect attacks using AI and work along two or more servers to improve availability and reliability. Syncplify.me also allows a high granular control using white lists, speed limits, virtual folders, key pairs per-use, etc.
Key Features:
- Highest Security: According to the website, this server has not been attacked even once since its inception, automatically identifying known and unknown attacks before they impact your system, and uses heuristics and AI to block hackers.
- Event Handling: Intercepts and handles over 45 events and performs many custom actions on them like sending emails, zipping files, and more. This level of automation reduces your time and effort.
- Availability: Multiple Syncplify server nodes can be run together to act as a single node from a performance and resilience standpoint. This option also balances your load better and ensures that your servers are always available for your users.
Why do we recommend it?
Syncplify.me is a commercial SFTP server that's never been hacked. Its powerful scripting and event handling are other benefits.
If your customized shell script is what produced the “sftp received message too long,” with Syncplify.me, you can run your scripts. They provide a fully-featured scripting framework along with an event-handling subsystem.
Who is it recommended for?
Works well for organizations that use Windows and Linux devices, and have to meet PCI-DSS and HIPAA compliance.
Pros:
- Good tech support
- Excellent integrations
- Automation saves time and effort
- Highly available
Cons:
- Documentation can be better
- Need a premium license if you go over 100 users
An evaluation version of Syncplify.me is available to download for free.
Final Words
In this post, you learned the main reason and how to solve the “sftp received message too long” error. A statement or message appears in the server’s bash terminal, interrupting the normal flow of the SFTP protocol. The cause is mainly TTY messages from incorrect user access, roles, MOTD, debug, etc.
To allow the standard SFTP session without interruption and fix the “sftp received message too long” appoint the user (with permission) to the appropriate bash terminal or profile or remove any statements or echos with a comment.
Troubleshooting SFTP received message too long FAQs
What causes the "sftp received message too long" error?
The "sftp received message too long" error can be caused by a number of factors, such as:
- Network congestion or latency
- Server resource limitations, such as memory or disk space
- Protocol mismatches between the SFTP client and server
- SFTP client or server configuration errors
How can I fix the "sftp received message too long" error?
To fix the "sftp received message too long" error, you can try the following:
- Increase the server's available resources, such as memory or disk space, to handle larger messages
- Check the SFTP client and server configurations to ensure they are compatible and configured correctly
- Use compression or data reduction techniques to reduce the size of the SFTP messages
- Split larger files into smaller segments before transferring them with SFTP
- Use alternative file transfer protocols, such as FTP or SCP
How can I prevent the "sftp received message too long" error?
o prevent the "sftp received message too long" error, you can try the following:
- Monitor server resources to ensure they are sufficient to handle the expected message sizes
- Use compression or data reduction techniques to reduce the size of SFTP messages
- Split larger files into smaller segments before transferring them with SFTP
- Use a different file transfer protocol, such as FTP or SCP, if SFTP is not suitable for the transfer requirements