USB Lockdown Software is also known as Device control software. These applications protect data against insider threats by controlling and managing data transfers across different removable storage devices. Removable storage devices, such as USBs, smartphones, WiFi network cards, printers, etc., are often used in organizations to easily supply and access information in various formats. However, […]
The Best USB Lockdown Software Tools
Catchpoint Review & Alternatives
User experience is a critical part of today’s digital world and an important metric to stay ahead of the competition. Let’s look at some statistics to understand its importance. 32% of customers leave a loved brand after just one bad experience. 88% of users don’t return to a website after a bad user experience. Every […]
What is Share and Storage Management for Windows Servers?
Businesses take modern business operations relatively seriously and, for this purpose, implement numerous services or tools for these servers. Earlier, file serving introduced networking to several organizations and continues to remain on the top in the list of business requirements. However, the file server is only the core function handled by the server. There are […]
What Is Cisco Prime Infrastructure?
As an IT professional, you know how daunting it is to simplify your ongoing online responsibility. Also, scaling networks across wired, wireless, and virtual IT environments makes network management more complex by asking network admins to get as much help as possible. Since networks play a pivotal role in serving the employees for administrative purposes […]
How to query FSMO roles in Active Directory Quickly
Organizations are constantly looking to enhance employees’ productivity by giving them quick access to the resources they need. But, at the same time, organizations are also wary of security and want to provide access to only those resources that employees need. Active Directory (AD) helps to strike a balance between these two objectives. It is […]
How to Force Group Policy Update Remotely
As the name suggests, Group Policy is a feature that controls the users’ working environment in an organization. It aims to provide a uniform look and feel and security features to all the computers and workstations. From an administrator’s standpoint, it gives them centralized control over the configuration and management of all the systems in […]
How to Install PowerShell Modules – A Step by Step Guide
PowerShell scripts are a popular choice for task automation because they are simple, human-readable, and easy to master. In this article, we will talk about PowerShell modules and their installation, but a touch on the basics. What is PowerShell? PowerShell is an automation and configuration management platform from Microsoft that eases the process of building, […]
Sciencelogic Review & Alternatives
Automation has become an integral part of today’s business operations because of the scale of data handling and processes and the speed at which products have to be delivered. Such automation is not possible without the right platform to support them, and one such platform that is well-known for its automation capabilities is ScienceLogic. This […]
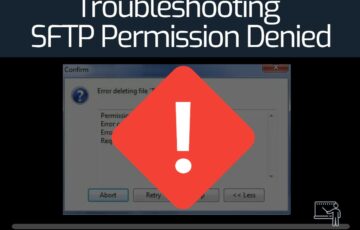
Troubleshooting SFTP Permission Denied
The SFTP Permission denied error happens when you SFTP into a server and try to add, remove or modify a file or directory. Still, the SFTP server does not allow you, and instead, it throws back permission denied, error: code 3. To solve the SFTP permission denied error, you’ll need to verify that the user […]
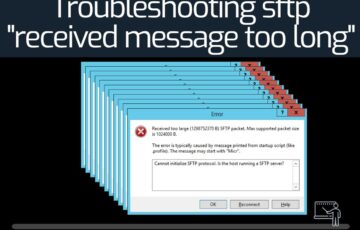
Troubleshooting sftp received message too long
When attempting to transfer files using the SFTP protocol, you get the message “Received message too long … ” in your Linux or macOS machine. Your Windows machine shows something similar: “Received too large (some number) SFTP packet”, “Max supported packet size is …”. The message means that the SFTP client received bad or unknown […]
The Best Log Parsing Tools
Every business generates thousands to millions of transactions per day, depending on the size of the business, nature of operations, number of applications, and more. Every aspect of every transaction is logged so that you can imagine the huge tons of logs generated each day. Here is our list of the best log parsing tools: […]
VictorOps Review & Alternatives
VictorOps, now called Splunk On-Call, is an incident response management system that sends alerts immediately, so you can remediate incidents before they impact the end-user. This robust tool takes a DevOps approach to incident management and, in the process, empowers you to collaborate with your team members to come up with the most effective solutions. […]
What is a Continuous Profiler?
While writing code, developers are constantly looking for ways to make them more efficient. In other words, they strive to achieve the desired output with as few lines of code as possible. However, this may not always be possible because of requirement changes, preferences and skills of developers who contribute to it, and more. This […]
7 Best Tools to Easily Run CI/CD Tests
Continuous Integration (CI) and Continuous Delivery (CD) are essential to help businesses deliver high-quality products quickly. These practices bridge the gap between development and operation by automating the process of development, testing, and deployment. These CI/CD practices are implemented using advanced tools and services. If you’re one such business looking to make the most of […]
The Best Tools for IoT Software Monitoring
The Internet of Things (IoT) is the next leap in technology, as it enables everyday physical objects to connect and exchange data with each other. This technology has opened a world of possibilities to provide seamless integration across the different aspects of life and work. Here is our list of the best tools that can […]
Sematext Review & Alternatives
Monitoring is a key aspect of every organization’s tech stack and activities as it helps to identify issues and troubleshoot them at the earliest. Also, it ensures you’re on top of the performance and availability of different components. However, the downside is that the monitoring process is time-consuming and effort-centric. So, how do you balance […]
The Best JavaScript Monitoring & Debug Tools
JavaScript is a popular scripting language that can be used both on the client and server sides to make web pages dynamic and interactive. This text-based language adds behavior to web pages and, in the process, improves the user experience of visitors who come to the web page. Here is our list of the best […]
The Best Tools for Snowflake Usage Monitoring
Data analytics is an essential and the most significant part of every business as it helps to optimize performance, try new avenues, improve efficiency, reduce costs, and more. In addition, the insights gleaned from data analytics will reflect across all areas of the organization and translate into better decision making, finding lucrative marketing opportunities, improving […]
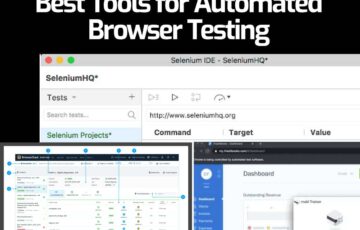
6 Best Tools for Automated Browser Testing
Providing a consistent user interface across different platforms and operating systems is the holy grail of UX design and development. However, this is not easy given that browsers tend to render information differently, which means there is a chance for the look and feel to change on different browsers. So, how do you ensure a […]
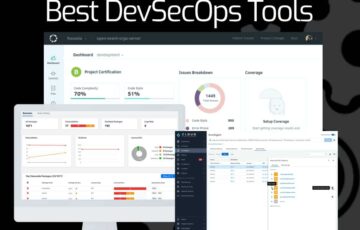
The Best DevSecOps Tools
Operations, development, and security are the three pillars of an organization’s everyday operations. These are often seen as separate fields that require extensive resources, but in reality, they are all interrelated and can be combined for greater efficiency and resource utilization. That’s what DevSecOps is all about. Here is our list of the best DevSecOps […]
The Best Tools to Monitor HAProxy Health
High-Availability Proxy (HAProxy) is a free and open-source utility used for load balancing in the cloud and also doubles up as a proxy server for HTTP and TCP-based applications. Here is our list of the best tools to monitor the health of HAProxy: AppOptics Application Performance Monitoring – FREE TRIAL One of the most popular […]
The Best Tools to Debug Python
Python is a high-level programming language often used for building desktop GUI applications, websites, and even web-based applications. It is one of the top ten programming languages in the world today, and its popularity stems from its simple syntax that makes your code highly readable. Here is our list of the best tools to debug […]
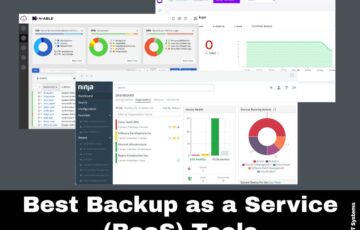
10 Best Backup as a Service (BaaS) Tools
Data is considered one of the greatest assets of any business. When data is misplaced or disappears from the system, the whole workflow gets devastated. It shows that data is the only thing that no one should ever mess up within the organization. However, one way to secure your data includes Backup as a Service […]
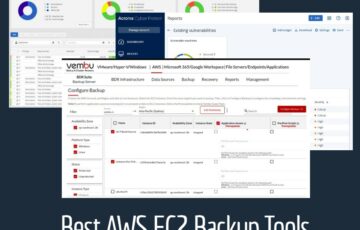
Best AWS EC2 Backup Tools
In the last decade, the world has seen exponential growth in the amount of data. Such is the volume that it has become difficult for some organizations to store and manage critical pieces of information on a regular basis. Here is our list of the best AWS EC2 Backup Tools: Vembu BDR Suite – FREE […]
The Best Database Backup Tools
Database backup tools help companies backup their critical databases to restore them as and when needed. Database backup tools are beneficial for organizations regardless of their size, as it helps mitigate employee errors, corrupted data, and broken hardware. In addition, it ensures your data is always available, even in case of primary database failure. Here […]
How to Configure Cisco Switches?
Switches are an important part of every network as they connect multiple devices such as computers and laptops with a LAN, enabling these devices to communicate with each other. Also, switches are critical to create a network of shared resources and improve the network’s security and performance. Cisco is the leading manufacturer of switches, and […]
The Best Data Center Monitoring Tools
Data centers are complex, and maintaining them requires a team of experts supported with the best monitoring tools. Such a combination can help to proactively identify issues and address them before it impacts the end-users. Also, they can prevent security lapses and the ensuing financial loss that could potentially run into thousands of dollars. That […]
9 Best MySQL Backup Tools
The MySQL database server has a unique storage-engine architecture, compatible with all major hosting providers, and carries many features that make it a top choice for many companies. For example, MySQL involves efficient management of deeply embedded applications, quick-start capability, robust transactional support, and more such features. In addition, MySQL Database helps deploy cloud-native applications […]
12 Best Azure Backup Tools
Microsoft Azure offers amazing products and cloud computing services to run and manage applications on a better level and create the future. Azure Backup is one of the services that include backup options for on-premises and cloud-based workloads, further preventing accidental damage to your data and helping to restore it in the Microsoft cloud. Here […]
Find Device or IP Address Using MAC Address
Every device connected to the network including, printer, switch, router, computer, tablets, and smartphones, has an IP address and Mac address that identify it on a network. Finding a Mac address is very easy if you know the IP address. But what if you don’t see the IP address of a device in a local […]
- « Previous Page
- 1
- …
- 3
- 4
- 5
- 6
- 7
- …
- 10
- Next Page »